Good afternoon, dear readers and guests of the blog site, in any organization there are always people who do not want to work and who use corporate resources for other purposes, I will give a simple example: you have a small office, let’s say 50 employees and an Internet channel with a bandwidth of 20 megabits and a monthly traffic limit of 50 GB, this is enough for the office for normal Internet use and building business work, but there are people who may want to download a movie for the evening or a new music album, and most often they use terrent trackers for this, let me I’ll show you how in Kerio Control 8 you can prohibit p2p traffic and set a daily traffic limit for an employee.
Blocking p2p traffic in Kerio Control 8
And so you have built a local network in which a malicious downloader has appeared, I think you will identify it immediately from the statistics logs, filter it by columns. Apart from the reprimand that will follow from the management, you are like System Administrator should prevent further attempts to download content via p2p traffic.

You have two options:
- Enable complete blocking of p2p traffic
- Set a daily limit per user
Let's start by blocking peer-to-peer traffic, go to the content filter and create a new rule. Click add and select "Applications and web content categories"

Find the download section and check the peer-to-peer network checkbox.

In the action, set the rules to delete.

In theory, to completely block p2p traffic, a created rule is enough, but I also advise you to set quotas for users if you have an Internet limit, in order to teach them to use it exclusively for work matters. To do this, go to the Users tab and in the properties of any on the "Quota" tab, specify the daily limit in megabytes.

To correctly configure traffic distribution, you must select the type of Internet connection.
For each local network the most suitable one is configured. Can be connected permanent access, with this function there is a constant connection to the Internet.
The second option may be to connect when necessary - the program itself will establish a connection when needed.
There are two connections; if the Internet connection is lost, Kerio Control will reconnect to another channel.
Having two or more Internet channels, you can choose a fourth connection type. The load will be distributed evenly across all channels.
: User setup

It is necessary to configure user access parameters; basic configuration of the program is required. You need to specify and add network interfaces, select network services available to users. Don't forget to set up rules for VPN connections and rules for services running on your local network. To add users to the program, we recommend that you first divide them into groups. This function can be set in the “Users and Groups” tab.
In groups, you need to create access rights, for example, the ability to use VPN and view statistics.
There is a domain on the network, adding users is very easy. You need to enable the “Use Domain User Database” option in the “Users” menu. There is no domain on the network; users must be added manually, giving each a name, email address, login and description.
Setting up statistics in

Kerio Control showed Internet traffic statistics; users need to be authorized.
You need to monitor user statistics; enable the browser to automatically register each user.
The company has a small number of employees; it is possible to set up a permanent IP for each computer and associate each user with it.
: Content filtering - setting options

To configure the security system, you need to go from the “Configuration” tab to the “Content Filtering” settings. In the “Antivirus” section, you can configure the update of anti-virus databases and use the checkboxes to select the protocols that will be scanned.
To enable HTTP traffic scanning, go to the “HTTP Policy” tab. Activate the “black list” and add prohibited words to it. Using the landmarks you added, the system will immediately block all sites on which these expressions appear. Create more flexible system filtering, create rules using the “URL Rules” subsection.
: Configure traffic rules

Traffic rules are configured through the “Configuration” section. Go to the “Traffic Policy” tab and select one of the three parameters that you want to configure. In the “Traffic Rules” section, you create rules that will be used to regulate user access to the Internet, content filtering, and connections from a remote office.
Give the rule a name. In the Source column, you can select Any Source, Trusted Source, or list specific sources. In the “Destination” column you need to indicate where the data will be sent, to a local network, VPN tunnel or the Internet. The “Services” item is intended to include in the list of all services and ports with the help of which a specific rule will be implemented.
Setting up load balancing

To control network traffic and rationally distribute it between the most important transmission channels, it is necessary to configure load balancing. Thus, Internet access for users is optimized. By distributing traffic on the most important connection channel for transmitting important data, there will always be uninterrupted Internet.
To assign the volume of network traffic, the program implements QoS support. You can create maximum throughput for a priority channel while stopping low priority traffic. It is possible to configure load balancing across multiple connections.
NAT: setting

Using the Kerio firewall, you can ensure a secure PC connection to your local network. Create Internet access for some employees in a remote office, without any action on their part. To do this, you will need to create a VPN connection on your local network from a remote office. Install and configure interfaces for connecting to the Internet. In the control panel, in the “Traffic Policy” tab, create a rule that allows local traffic.
Don't forget to indicate all the required objects in the source. You will also need to create a rule that will allow local users Internet access. You need to configure NAT, despite the created rules, Internet access will not be possible without enabling this function. In the “Traffic Policy” tab, select the “Broadcast” section and check the “Enable NAT source” checkbox. Specify the balancing path.
: setting up interfaces


The interfaces are configured immediately after installing the program. Having already activated the one that was purchased from and chosen the type of Internet connection, you can start setting up interfaces. Go to the “Interfaces” section on the management console. The program itself detects interfaces that are connected to the Internet and accessible. All names will be displayed in the form of a list.
If the load on the interfaces is distributed (selecting the type of Internet connection), you can add network interfaces in an unlimited number. The maximum possible load is set for each of them.
Video
Improper management of bandwidth in an office network (or lack of such management) leads to noticeable interruptions: the Internet is slow, the quality of voice and video communications decreases, etc. This will help you correctly prioritize and ensure sufficient bandwidth for important traffic.
About Kerio Control features
The Kerio Control software solution belongs to the UTM (Unified Threat Management) class of products and provides comprehensive protection for workstations and servers when working on the Internet. The solution is aimed at medium-sized corporate networks and is descended from the well-known WinRoute product. The words “comprehensive security” mean that Kerio Control consists of many modules responsible for different aspects of security, namely:
- firewall;
- router;
- intrusion detection and prevention system (IPS/IDS);
- anti-virus traffic protection;
- traffic content filtering;
- monitoring and analysis of user activity on the Internet;
- two VPN servers- one based on its own protocol and the second based on an open standard IPSec VPN;
- Bandwidth management and QoS support.
In this article we will talk about the last item on this list, but not the least important.
Problems of optimizing Internet access
Let's look at several typical scenarios.
First: the manager needs unlimited access to bandwidth, better than others. By the way, it is not necessary for the manager - a guaranteed wide bandwidth will be required for the server that replicates the database with a remote data center.
Second: managers complain about poor hearing and dropped calls. Or the payment terminal accepts the card payment the third time because it cannot contact the bank.
Third: The speed of the entire office suddenly dropped. It's time to check who is downloading torrents at work.
All of these scenarios require bandwidth management, such as prioritization and anomaly detection. Management tasks will look something like this:
- required for VoIP throughput 10 Mbit/sec, no less, at any time;
- streaming data should not consume more than 100 kbit/sec;
- guest traffic must be separated from worker traffic and not switched to a backup channel in case of failure of the main one;
- privileged traffic is more important than regular traffic during business hours.
To formalize each of these tasks, we need to determine why and by what criteria we prioritize.
Types of traffic. In the first place are online video conferencing, telephony, video signal transmission, VPN, here bandwidth is very important. On the second - normal access to sites, files, mail. The lowest priority can be set for accessing entertainment sites, shopping, etc.
Access time. Different priorities can be set for working hours and non-working hours. You can give high priority to the server for the data replication period and limit the rest.
Rule = formalized constraint
Once the listed criteria are defined, you can move on to the band limit rules. Let us explain using the example of the Kerio solution for transport, used, for example, on ships. If the ship has satellite channel with expensive traffic and a narrow bandwidth and a wide channel available at the ports, it is clear how to prioritize. For example, like this:
Actually, this is already quite a rule in Kerio Control.
Now let's return from the ship to the office and look at the example with IP telephony. If the band is congested, it reduces quality voice communication, which means we’ll set priorities like this:
And these are also three rules in Kerio Control.

Similarly, the rules solve problems of guaranteed wide bandwidth for management and equipment, restrictions on guest connections, etc.
Bandwidth management in Kerio Control
On the Kerio Control control panel at the top you can see a list of available Internet interfaces. For example, a fast channel and a slow one. Below it are local networks, for example, main and guest.

Now we need to match Internet interfaces to local networks, which we will do on the “Traffic Rules” tab. For example, we assign our own interface (the cheapest) to the guest network, and guests do not clog the main office network. Here we also configure restrictions on traffic types, for example, only web access for guests and any traffic for our own.

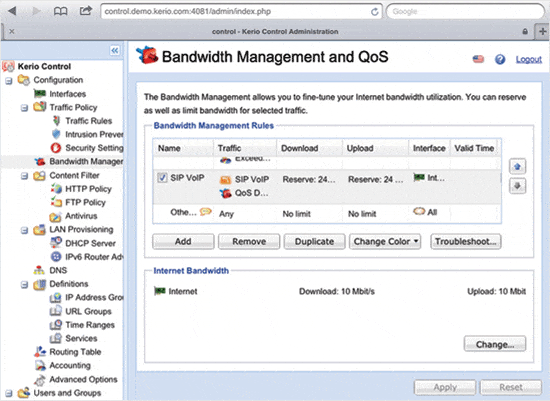
Now that interface routing is configured, it's time to prioritize bandwidth usage. We go to the Bandwidth Management and QoS tab, create a rule for VIP users, add to it the pre-created groups Owners (the same VIP users) and Equipment (which definitely need a good connection), and set, for example, to reserve 20% of the bandwidth.

An important point - this 20% is counted from the band specified in the settings! Here it is important to put not the figure stated by the provider, but the actual throughput.
Now we create a rule for critical traffic and add traffic types to it: SIP VoIP, VPN, instant messages and remote access.

And we will reserve for him, for example, 3 Mbit for downloading and uploading.
Then we'll create a rule for important traffic and include traffic types such as web browsing, mail, multimedia, and FTP. And we will set a limit on consumption of no more than 50% of the bandwidth, and only during working hours.

Now let's create a rule for harmful traffic. If, when selecting a traffic type, you click in the “Connection that satisfies a content rule” menu, you can use the content filter and select social networks, stores, traffic, games, etc. You can also limit P2P. Give them a strict limit of 256 kbit and let them download.

Now let's look at guest users. The Active Hosts tab makes it easy to see what's happening right now. It is likely that you will find a guest who has already downloaded a gigabyte and continues to use your Internet at decent speed.

Therefore, we make a rule for guests. For example, do not exceed 5% of the band.

And further. As you remember, we direct guests to a specific network interface. A bandwidth limiting rule can be configured to either limit the limit on one specific network interface or on all network interfaces. In the latter case, if we change the interface associated with the guest network, the rule will continue to apply.

AND important point. The rules work in the order they appear in the list, from top to bottom. Therefore, it makes sense to put rules that filter out many access requests at the beginning.
All this is described in detail in articles on the knowledge base of Kerio.
- Setting the speed of the link (KB 1373)
- Configuring bandwidth management (KB 1334)
- Configuring policy routing (KB 1314)
- Monitoring active hosts (KB 1593)
Before and after optimization
Before. All traffic passed on equal terms, without priorities. In the event of a traffic jam, all traffic, including critical traffic, suffers.
After. Important traffic is given priority. Restriction and reservation mechanisms are configured by user type, traffic type, and time.
Instead of a conclusion
We've seen that it's easy to restrict access to bandwidth using custom rules. It is the ease of use of its products that Kerio considers its most important advantage and has maintained over the years, despite their increasing complexity and functionality.
Kerio Control falls into that category software , which combine a wide range of functionality with ease of implementation and operation. Today we will look at how this program can be used to organize group work among employees on the Internet, as well as reliably protect the local network from external threats.
belongs to the category of products in which a wide range of functionality is combined with ease of implementation and operation. Today we will look at how this program can be used to organize group work among employees on the Internet, as well as reliably protect the local network from external threats.
The implementation of the product begins with its installation on a computer that plays the role of an Internet gateway. This procedure is no different from installing any other software, and therefore we will not dwell on it. We only note that during this process some Windows services, interfering with the operation of the program. After the installation is complete, you can proceed to configuring the system. This can be done either locally, directly on the Internet gateway, or remotely, from any computer connected to corporate network.
First of all, we launch through standard menu "Start"management console. It is used to configure the product in question. For convenience, you can create a connection that in the future will allow you to quickly connect to. To do this, double-click on the item" New connection", indicate in the window that opens the product (Kerio Control), the host on which it is installed, as well as the user name, and then click on the button " Save as" and enter the name of the connection. After this, you can establish a connection with. To do this, double-click on the created connection and enter your password.
Basic setup of Kerio Control
In principle, all operating parameters can be configured manually. However, for initial implementation it is much more convenient to use a special wizard that starts automatically. At its first step, you are asked to familiarize yourself with basic information about the system. There is also a reminder here that the computer running Kerio Control must be connected to the local network and have a working Internet connection.
The second stage is choosing the type of Internet connection. There are four options available here, from which you need to choose the most suitable one for your specific local network.
- Permanent access – the Internet gateway has a permanent connection to the Internet.
- Dial-on-demand - will independently establish an Internet connection as needed (if a RAS interface is available).
- Reconnect on failure – when the Internet connection is lost, it will automatically switch to another channel (two Internet connections are required).
- Channel load balancing - will simultaneously use several communication channels, distributing the load between them (two or more Internet connections are required).
In the third step, you need to specify the network interface or interfaces connected to the Internet. The program itself detects and displays all available interfaces in the form of a list. So the administrator can only choose suitable option. It is worth noting that in the first two types of connections you need to install only one interface, and in the third - two. The setting of the fourth option is slightly different from the others. It provides the ability to add any number of network interfaces, for each of which you need to set the maximum possible load.
The fourth stage is to choose network services, which will be available to users. In principle, you can select the option " No limits". However, in most cases this will not be entirely reasonable. It is better to tick off those services that are really needed: HTTP and HTTPS for browsing websites, POP3, SMTP and IMAP for working with mail, etc.
The next step is to configure rules for VPN connections. To do this, only two checkboxes are used. The first determines which clients users will use to connect to the server. If they are “native”, that is, released by Kerio, then the checkbox must be activated. Otherwise, for example when using built-in Windows Tools, it needs to be disabled. The second checkbox determines the possibility of using the Kerio Clientless SSL VPN function (managing files, folders, downloading and uploading via a web browser).
The sixth step is to create rules for services that run on the local network, but must also be accessible from the Internet. If you enabled Kerio VPN Server or Kerio Clientless SSL VPN technology in the previous step, then everything necessary for them will be configured automatically. If you need to ensure the availability of other services (corporate mail server, FTP server, etc.), then for each of them click on the button " Add", select the name of the service (standard ports for the selected service will open) and, if necessary, specify the IP address.
Finally, the final screen of the setup wizard is a warning before the rule generation process begins. Just read it and click on the " Complete". Naturally, in the future, all created rules and settings can be changed. Moreover, you can either re-run the described wizard or edit the parameters manually.
In principle, after completion of the work the wizard is already in working order. However, it makes sense to slightly adjust some parameters. In particular, you can set limits on bandwidth usage. It gets clogged the most when transferring large, voluminous files. Therefore, you can limit the download and/or upload speed of such objects. To do this, in the section " Configuration"need to open section" Bandwidth limit", enable filtering and enter the bandwidth available for large files. If necessary, you can make the limitation more flexible. To do this, click on the " Additionally" and specify in the window that opens services, addresses, and time intervals for filters. In addition, you can immediately set the size of files that are considered large.
Users and groups
After initial setup system, you can begin adding users to it. However, it is more convenient to first divide them into groups. This will make them easier to manage in the future. For creating new group go to the section " Users and groups->Groups" and click on the " button Add". This will open a special wizard consisting of three steps. In the first step, you need to enter the name and description of the group. In the second, you can immediately add users to it, if, of course, they have already been created. In the third step, you need to define the rights of the group: access to system administration, the ability to disable various rules, permission to use VPN, viewing statistics, etc.
After creating groups, you can proceed to adding users. The easiest way to do this is if a domain is deployed on the corporate network. In this case, just go to the section " Users and groups->Users", open tab Active Directory, enable checkbox " Use domain user database" and enter the login and password of an account that has the right to access this database. In this case, it will use Accounts domain, which, of course, is very convenient.
Otherwise, you will need to enter users manually. For this purpose, the first tab of the section in question is provided. Creating an account consists of three steps. On the first one you need to set your login, name, description, address Email, as well as authentication parameters: login and password or data from Active Directory. In the second step, you can add the user to one or more groups. At the third stage, it is possible to automatically register an account to access the firewall and certain IP addresses.
Setting up a security system
It implements ample opportunities to ensure the security of the corporate network. In principle, we have already started protecting ourselves from external threats when we set up the firewall. In addition, the product in question implements an intrusion prevention system. It is enabled by default and configured to optimal performance. So you don't have to touch it.
The next step is antivirus. It is worth noting that it is not available in all versions of the program. To use anti-malware protection, it must be purchased with a built-in antivirus, or must be installed on the Internet gateway external module antivirus. To enable antivirus protection you need to open the section " Configuration->Content Filtering->Antivirus". In it, you need to activate the module being used and use checkboxes to mark the protocols being checked (it is recommended to enable all). If you are using a built-in antivirus, then you need to enable updating the anti-virus databases and set the interval for performing this procedure.
Next, you need to configure the HTTP traffic filtering system. This can be done in the section " Configuration->Content Filtering->HTTP Policy". Most simple option filtering is the unconditional blocking of sites that contain words from the “black” list. To enable it, go to the " tab Forbidden words" and fill out the list of expressions. However, there is a more flexible and reliable filtering system. It is based on rules that describe the conditions for blocking user access to certain sites.
To create a new rule, go to the " tab URL Rules", click right click mouse on the field and select in context menu paragraph " Add". The window for adding a rule consists of three tabs. The first one specifies the conditions under which it will be triggered. First, you need to select who the rule applies to: all users or only specific accounts. After this, you need to set the criterion for matching the URL of the requested site. To do this, you can use a string that is included in the address, group of addresses or rating of the web project in the Kerio Web Filter system (essentially, the category to which the site belongs). Finally, it is worth indicating the system’s reaction to the fulfillment of conditions - allow or deny access to website.
On the second tab, you can specify the interval during which the rule will apply (by default, always), as well as the group of IP addresses to which it applies (by default, all). To do this, you just need to select the appropriate items in the drop-down lists first set values. If time intervals and groups of IP addresses have not yet been set, then using the "Edit" buttons you can open the right editor and add them. Also on this tab you can set the program’s action if the site is blocked. This can be by issuing a page with a given refusal text, displaying a blank page, or redirecting the user to a given address (for example, to a corporate website).
In the event that the corporate network uses wireless technologies, it makes sense to enable a filter by MAC address. This will significantly reduce the risk of unauthorized connection various devices. To implement this task, open the section " Configuration->Traffic Policy->Security Settings". In it, activate the checkbox " MAC Address Filter Enabled", then select the network interface to which it will be distributed, switch the list of MAC addresses to " Allow only listed computers to access the network" and fill it out with the details of wireless devices owned by the company.



















Let's take stock
So, as we see, despite the wide functionality, using it to organize group work of corporate network users on the Internet is quite simple. It is clear that we only considered basic setup this product.