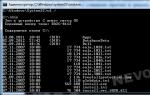
The easiest way to check MD5 (hash sum) in Linux is in the terminal. Through any GUI it will be necessary to do more manipulations than just command Linux terminal following:
Md5sum /home/pavel/Distributions/lubuntu-12.04-desktop-i386.iso
It goes without saying that the path to the file you need (/home/pavel/Distributions/lubuntu-12.04-desktop-i386.iso) must be specified as your own, the one that corresponds to the desired object for counting MD5 amounts in Linux.
To avoid entering the path to the file manually, you can copy it as follows. Using the file manager, we go to the directory where the file we need is actually located. Address bar V file manager it is necessary to transfer from the “icon” view to the text view, using the keys
$ md5sum /home/pavel/Distributions/lubuntu-12.04-desktop-i386.iso /home/pavel/Distributions/lubuntu-12.04-desktop-i386.iso
Commands in Linux are standard for everyone and means that the command md5sum suitable for any distribution Linux, no matter where you are. This is one of the advantages of the command line!!!
MD5 (hash) verification required after download large files, which will not work properly if any files are damaged or changed in some way. Checking MD5 amounts is mainly applied to .iso files, most often to distribution kits. If the .ISO file is damaged, then you should not write it to a USB key (flash drive), much less to an optical disk; the Linux distribution will report an error in any files during installation.
After recording Linux distribution you need to check the integrity of the optical disk and find out its MD5 sum
In this article, we will continue to delve into the world of the command line and compare the MD5 of the recorded optical with the MD5 sum of the original .ISO file using the isoinfo console utility. To begin with, we will extract some primary information about the recorded disc with the command:
Isoinfo -d -i /dev/sr0
Where /dev/sr0 is a DVD-ROM, to clarify the name of your mounted optical disk, in case you have more than one, you can find it from the output of this command:
From the available information after entering:
$ isoinfo -d -i /dev/sr0
There will be something like this:
CD-ROM is in ISO 9660 format System id: Volume id: Lubuntu 12.04 i386 Volume set id: Publisher id: Data preparer id: XORRISO-1.0.8 2011.04.14.073001, LIBISOBURN-1.0.8, LIBISOFS-1.0.8, LIBBURN -1.0.6 Application id: Copyright File id: Abstract File id: Bibliographic File id: Volume set size is: 1 Volume set sequence number is: 1 Logical block size is: 2048 Volume size is: 352406 El Torito VD version 1 found, boot catalog is in sector 320 Joliet with UCS level 3 found Rock Ridge signatures version 1 found Eltorito validation header: Hid 1 Arch 0 (x86) ID "" Key 55 AA Eltorito defaultboot header: Bootid 88 (bootable) Boot media 0 (No Emulation Boot) Load segment 0 Sys type 0 Nsect 4 Bootoff 52A18 338456
These lines are important to us:
Logical block size is: 2048 Volume size is: 352406
Dd if=/dev/sr0 bs=2048 count=352406 conv=notrunc,noerror | md5sum -b
Pay attention to three points that you must substitute:
- /dev/sr0 - path to the optical disk (if you have one, then this item is unchanged)
- bs= 2048 - you have your own value “Logical block size is:”
- count=352406 - from the value “Volume size is:”.
After calculation you will get something like this:
352406+0 records read 352406+0 records written copied 721727488 bytes (722 MB) *- , 55.3223 s, 13.0 MB/s
- this is the MD5 sum of the disk. If it matches the value indicated on the site where you downloaded the file or with the source file on your computer, then the disc was recorded without errors. In practice, it happens that the MD5 sum often does not coincide with the MD5 sum indicated on the website due to errors when reading the disk.
So you've been downloading long and hard Windows image, and now you want to make sure that not a byte was lost along the way. Or the distribution package was brought to you by the good fairy, and you want to check if it is connected with pirates. To determine the integrity of the distribution you will need two things - check sum and a program to check it.
Windows image checksums
Upd. 2017. Microsoft has moved downloads from MSDN to a new site, https://my.visualstudio.com/downloads, where a subscription is required to access the images. Therefore, without subscribing using the method below, it is no longer possible to find out the checksum.
Microsoft publishes their product checksums on MSDN, specifying SHA1 as the hash type. Search for the language version and edition of your Windows and click Intelligence to see the checksum below.
That's half the battle.
Checksum verification using the built-in certutil utility
If you do not specify the parameter -sha1, the utility will calculate the MD5 hash.
As you can see, everything is very simple! You can use this method to verify the MD5 or SHA1 checksums of any files.
Checksum verification using HashTab program
If the command line scares you, there is an easier way to check the checksum.
- Download and install the HashTab program.
- Click right click mouse on the image file and select "Properties".
- Go to the "File Hashes" tab.

When exchanging information via computer networks or through portable media, the actual question arises of how to check the integrity transmitted information. After all, if several bits are incorrectly saved in the resulting multi-megabyte file, this can lead to problems when using this file. Especially if this file is an application. Therefore, with the spread of various installation files, and other information, it is customary to indicate a checksum (hash) - so that users, having downloaded data, can independently check the checksums of the files for a match with the hash of the downloaded information.
Principles of using checksums
To use the technology intelligently, it is useful to understand what a hash is. In general, a hash is a set of bits obtained as a result of calculations on information using a specific algorithm. Distinctive feature This algorithm is that when at least one bit in the original information changes, the hash sum also changes. And at the same time, there is an extremely low probability that a random change in a few bits of incoming information will leave the hash unchanged. Thus, it turns out that the checksum is like a data passport, after checking which you can conclude that the data is genuine.
Therefore, the principle of using hashes is quite simple, and consists of two stages:
1. Calculate, store and publish the checksum of the original data.
2. Calculation of its value for a copy of the data and comparison with the value for the originals.
There are many different hashing algorithms. And accordingly, there are many types of hash sums. The most popular among them are CRC32, MD5, SHA-1 etc.
Where are hashes used?
Even those users who do not know what hash sums are still quite often benefit from their use - for example, when opening packed files. The fact is that modern archivers add their hashes to packed files. They can be seen by opening the archive using an archiver program.
And accordingly, when unzipping, these hashes are automatically verified. If the archive is damaged, the archiving program will generate an error with a message that the checksums of the files do not match. Therefore, the easiest way to ensure control over the correct transfer of files is to pack them into an archive.
Another area where checksums can be used is to use them instead of passwords. When a visitor registers on a website by entering a secret password, it is not the password itself that is stored on the server, but its hash. Accordingly, if attackers gain access to the server, they will not be able to find out the saved passwords - they simply are not there.
Also, hash sums are an integral part of the work of torrent trackers. Thanks to this, when downloading files via torrents, 100% integrity of information transfer is guaranteed. In this case, the user does not need to control this process in any way. All necessary operations during downloading are carried out by the program (). Of course, if the files have been downloaded for a long time, and you need to make sure that they have not become damaged over time, you can run a manual re-scan. For example, in the uTorrent program there is a special item for this in context menu(appears when you right-click on the selected torrent).

When using archives and torrents, hashing is carried out without user intervention. But since not all files are convenient to archive, much less use torrents when sending information, there is a widespread practice of calculating checksums for an arbitrary set of files. Most often, a hash in MD5 format is used for this, for which many different programs have been created.
How to create MD5 hash of files using MD5Checker?
Despite the fact that the MD5 algorithm is available in many file managers and utilities, not all of them are convenient to use. Some programs cannot check hashes for a group of files. Another part of the programs, although it does this, does not display a report on the scan results in a convenient form - you have to manually scroll through the entire list of files to identify error messages.
The only maximum convenient program for working with MD5 - this is the MD5Checker application. You can download the program from official website. Despite the fact that the program has an English-language interface, it is quite simple to use.
The program is set to hashing by default program files, archives and ISO images. Therefore, if you want to use this application for music and video, you must first change one single setting - specify a mask for the files with which the program will work. To do this, go to the “Tools / Options” menu item and specify the * symbol (which means “all files”) in the “Include” field.


After this, you can use the program as usual - now every single file in all subfolders will be scanned.
To create an MD5 hash, you need to drag selected files from a folder into the program window - and the program will automatically begin to calculate MD5 sums for all selected files and all files in subfolders (that meet the mask we specified). The calculated amounts will be displayed in the “Current MD5” column. Now all that remains is to save the obtained values to a file by clicking the “S To” button (“Save to”).

It is important to note that if you save the MD5 file in the folder in which all the files and subfolders we selected are located, the relative paths to them will be saved. This will allow you to check the checksum in the future even if you move files to another location. Therefore, before saving the file, it makes sense to go to the root of the folder by clicking the corresponding button.

If you open the resulting file in Notepad, you will see that the information is stored in it in plain text.

In this case, you can make sure that the paths to the files are relative, i.e. do not contain the drive letter on which they are located. Such an MD5 file can be stored in a folder along with files, and in the future the integrity of the files in this folder can be checked on any computer.
How to check file checksums?
To check the checksums of files, you need to restart the program or click the “Clear” button to clear the list of files.

After this, you should drag the MD5 file into the program window and make sure that a green checkmark appears next to each file. This means that the files are kept safe and secure. If there are quite a lot of files, then it is more convenient to control using the “Failed” and “Passed” counters in the table header.

You can conduct an experiment: rename one of the files, and edit another one, making a couple of minor changes. After running the re-check, the program discovered that one of the files had become inaccessible under its original name (marked with a yellow icon), and the checksum of the second file did not match (marked with a red icon). A checksum mismatch indicates that the file has either been modified or is damaged.

It is worth noting that if you have several folders, each of which contains one or more MD5 files (including in subfolders), then by dragging all these folders into the program window, you can check all the files for integrity in one fell swoop. MD5Checker automatically extracts hash values from files with the md5 extension encountered during scanning. This can be extremely convenient if large amounts of information are copied or transmitted over the Internet.
Also, if you have renamed or moved some files to another location, you can edit the MD5 file in Notepad, specifying new values for their paths there - and then you can use it further to check the files.
Results
Hashing technology provides a unique opportunity to control the safety of information. In modern times, when the number of user files is in the thousands and tens of thousands, convenience in processing hash sums for large amounts of data is necessary. The MD5Checker program successfully copes with this task, with which you can both check checksums and create them for many files, regardless of the depth of their nesting in the folder tree.
Article content:
In some situations, it may be necessary to calculate the MD5 hash for a file that you have downloaded to your computer. For example, to be sure that you downloaded exactly the file you wanted and the attacker did not modify it. In this article we will look at 2 different ways do this: through the extension for Explorer, and also through command line.
Option via File Explorer extension
For Windows Explorer there is a wonderful Hashtab program, which is free for non-commercial use. You can download it from . Select the free version and click on the "Download" button.

After installing the program, the Explorer context menu will appear new inset“File hash sums”, by selecting which, the program will automatically calculate hash sums for the selected file depending on which algorithms are selected in its settings. 
Command line option (with program installation)
If we need to calculate the hash amount of a file via the command line, we can use a utility from Microsoft, which is suitable just for such cases. Download it from and install it. To do this, you will need to create a folder on your hard drive and specify it during the installation process. In our example, the program was installed in the C:\Program Files (x86)\FCIV folder. In order to calculate the MD5 hash of a file, we need to launch the command line and type the following command in it:
"C:\Program Files (x86)\FCIV\fciv.exe" -md5 C:\Users\Admin\Downloads\HashTab_v6.0.0.34_Setup.exe

As you can see, the MD5 hash sum is the same for both the first and second options.
"C:\Program Files (x86)\FCIV\fciv.exe" is the path to the fciv.exe file
-md5 - specifying the algorithm by which fciv.exe will calculate the hash sum
C:\Users\Admin\Downloads\HashTab_v6.0.0.34_Setup.exe - path to the file for which we calculate the hash sum.
Command line option (without installing programs)
In the event that you do not want to install any programs, you can get by with the built-in ones. using Windows, for this you can use the CertUtil utility.
Verifying the download is correct file from the archive using the Total Commander program
Program " Total Commander" is a multifunctional analogue of "Explorer" in Windows; checking md5 sums is simply built into it as additional function. Especially for checking md5 sums so large install the program, of course, there is no point. But if you already have it, you can use it to check whether the file was downloaded correctly.
1. Open in the Total Commander window the directory with the file to be checked and the reference md5 sum for it and left-click on the desired md5 file (in this case it is the only one):
2. From the Files menu, select "Verify CRC Checksums":
3. Wait for the verification process to complete:
4. Now, if in the report window you see “OK” to the left of the name of your file
This means that everything is in order and the file was downloaded correctly. If the report looks something like this:
This means the file is damaged and you will have to download it again.
Attention! Total Commander creates checksums in its own format, they can only be verified by itself. Therefore, try not to use this program to create checksums unless you are sure that those who will check the correctness of the download have Total Commander installed.
1. Open the directory with the desired file/files in the Total Commander window:
2. Select the required files: