This decision allows you to anonymously surf the Internet. The Tor program protects the user's Internet from external surveillance and hides his behavior and interests from third parties. Journalists, bloggers, dissidents, non-governmental organizations and others who want to maintain their own privacy and anonymity use Tor, a powerful tool for protecting against data flow analysis. The program supports working with various existing browsers, clients remote access, download managers and instant messaging systems without revealing the true location.
How to ensure anonymity
Providing personal freedom, anonymity and confidentiality with the Tor program is based on building a chain between encrypted connections and network servers. The communication session is fragmented through numerous servers located in different parts of the world, and each server knows from whom and to whom it transmitted the information, but not a single server knows the complete path from the user to the target.
Fast anonymizer
In order for the connection speed to be high, the program creates a 10-minute session for each unique connection chain, which also helps to confuse the traces.
 |
Definition:
Anonymity is Namelessness, obscurity; silence, hiding the name.
Solution:
There should be nothing in the way between you and the Internet that can tie you to your connection. And you can't act as usual. In this case, your usual behavior at the same time should be recorded falsely.
You can find out who you are
1) Financial trail
purchasing devices and services that provided your access to the Internet
receiving benefits from the Internet in the form of finance, goods and services
2) Electronic trail
IP, MAC, time, built-in cameras, wifi, gsm, gps, microphone.
operating systems, programs, plugins, etc.
these little people scurrying around with mobile phones containing software for collecting information not only about the owner of the mobile phone but also about the surrounding radio air. GPS coordinates, base stations GSM, WiFi hotspots, bluethooth devices, etc. And there the blonde is talking on the phone, and her camera is quietly filming that you looked in her direction. This is not because it is a spy, but because it puts everything on the phone indiscriminately.
3) Metadata trail
handwriting: speed, characteristics Your work on the Internet. The typing style on the keyboard has its own imprint. Spelling errors, correctable typos, punctuation, etc. The Google search string in any browser using JS (if allowed) is transmitted to the Google server continuously while you are typing. Consider that information about the nature of the set is transmitted to the Internet. Google does everything to know your face even if it is wearing a mask. Don't forget about the mouse or touchpad.
the information you are looking for without an anonymous mask can give you away if you try to do the same in a mask. You need to have clearly written instructions on what not to do and clearly limited actions. Your anonymous life should be similar to the everyday life of a spy. This is self-discipline, this is work, this is a constant replenishment of knowledge and its application in practice. It is very difficult not to get burned in practice when they are watching you for 24 hours and do it without straining.
With regret, let’s keep silent about the fact that your friends will carefully write your name, date of birth, relationship, photo next to your Nickname or phone number and upload it to Apple or Google, and all applications that have access to the address book (and only the lazy don’t go there) know this immediately .
You can steal an Internet connection, buy a SIM card with GPRS from gypsies, but how can you hide from the video cameras carefully placed all over the world? RFID chips from banks, libraries, and the metro are carefully placed in your pockets. The ID card becomes biometric and its presence in a pocket in a public place is enforced by law.
The more modern the computer and phone, the more likely it is to have a factory backdoor at the chip level, or a backdoor from a reseller or delivery service. You think that by installing Tails or Kali Linux you have solved the problem - you are mistaken, you also need to assemble a computer using lamps :). Or you carry your phone with you; it gives the provider information about where you were 24 hours a day. Gives him your daily habits. Here Vasya is going to work, here he is coming back from work. But suddenly Vasya disappeared from the radar, although usually at this time he travels along route A or B. Strange. Anomaly. And now if all this information falls into one hand and is analyzed, what happens? It turns out that the circle of suspects is sharply narrowing. Vasya is found on cameras in Mitino, buying a SIM card from a gypsy, or standing near the library in a car with a laptop on his lap.
And the fact that Vasya uses TOR, VPN and an unusual operating system is no secret to the provider. He just doesn’t care about Vasya for the time being. Recorded traffic can be opened later.
So I'll sign the words Artem
If you want anonymity on the Internet, do not use the Internet.
In this article we will talk about all aspects related to anonymity on the Internet so you can maintain your privacy while browsing the Internet:
We're not saying that you can become completely anonymous, that's practically impossible. But what we can actually do is try to make online interactions more hidden.
Stay incognito
Private browsing mode or incognito mode is a feature that is the second most popular browsing option in browsers. It is quite suitable for those cases when you access the Internet from someone else's computer and want to check your Facebook, Twitter or email accounts.Likewise, it is ideal for testing sites that are heavily loaded with cookies. And also for those cases when the computer you are working on has public access.
Private browsing does not completely erase your fingerprints. Individual elements, such as DNS lookups and some cookies, may remain after the session. So it's better to consider programs for anonymity on the Internet as a temporary measure. The main thing I want to draw your attention to is do not save your browsing history on a public computer.
If you want the best example, then open a private browsing session and browse a few sites, then exit the session, go to command line and enter the following:
Ipconfig/displaydns and press Enter.
This will be a list of all cached DNS entries visited from your computer, regardless of whether you used a private browsing session or not.
To delete entries, enter the following command:
Ipconfig/flushdns and press Enter.
This will clear the list and prevent any attempts to access it. It is also advisable to configure batch file, which will launch the browser in mode private browsing, and when closing automatically clear DNS records. This method can be used to maintain a certain level of privacy.
False identity
Using a fake identity sounds more intriguing than it actually is, but in many cases it is quite effective for achieving anonymity on the Internet:
Consider this example: you use the address Email to login to Facebook, Twitter, eBay and online games. This may seem quite reasonable, but for the hacker the task is now much easier. He only needs to hack one account or track you. But if you had many aliases, it would take a hacker much more time and effort to track down all the fake identities and identify the real user.
It's a simple concept, but it can be used to great effect to disguise your online activity. There have been cases of people using over fifty fake names and email addresses to log into websites to avoid identifying their real identity.
There are few reasons to provide your real identity online. Most sites only collect and sell your data, or use it for advertising purposes, so under no circumstances provide your real address email, home address or contact information on public sites:
If using fake identities is a hassle and you need something like a fake identity generator, you'll find it here.
How to maintain anonymity on the Internet? This site can completely create a fake identity with names, addresses, email addresses and phone numbers. He may even provide you with a number of fake credit cards, mother's maiden name, vehicle, blood type, height, weight and QR code, which can be used on not very reliable sites. It is obvious that all data provided is fake and any resemblance to real person is random.
The fake name generator also creates a fake email address that is working and you can use it to receive one-time email verification links. However, you cannot be sure who is also using this service. Nobody knows who else has access to this system. So it's better to think of it as a tool for generating email addresses that can be used to fill out various online forms.
Tools that help you stay invisible
There are a number of programs that can be used to hide your activities, erase your digital fingerprints, or remain invisible on the Internet. The most famous of them is the Tor Network. But those who need more high level encryption and anonymity, may consider using a VPN ( Virtual Private Network).
Tor Network
Tor is program for anonymity on the Internet in Russian, through which your online connections are passed through connected networks, each of which is owned by volunteers from around the world. The essence of this concept is to block the ability to track a user and find out his location, and give you the opportunity to visit blocked sites:
Tor Browser Bundle is free package for Windows, Mac and Linux, which when launched automatically connects you to the Tor Network and also launches a specially designed and modified version of Firefox.
Once the package is launched, when you start browsing sites through Tor, all content you connect to is transferred encrypted and passed through the network system mentioned above. Tor Browser Bundle works effectively with any TCP instant messaging, remote login, and other browser applications. However, this product does not guarantee 100% anonymity and should not be used to download illegal music or movies. This can cause congestion on the Tor network and cause problems for users who use the package for proper purposes.
The protocols used by P2P sites can often be used to scan an IP address, and will allow you to figure out your actual IP address, not the one generated by Tor.
However, Tor is a great product that you can use to stay anonymous. Built-in Firefox version, based on Extended Support Release ( ESR) Firefox by Mozilla, specially modified to optimize security and privacy features. To achieve this, access to the Components.interfaces element, which can be used to identify the user's computer platform, was blocked. With the exception of some Flash add-ons, caching of SSL sessions is prohibited and DNS information leakage via WebSockets is blocked.
By using the Tor Browser Bundle, you will be relatively protected from online snooping ( except for the most cunning attackers). Although ensure complete anonymity on the Internet you won't be able to:
If you look at the above screenshot, you will see that by navigating through Tor, your IP address is hidden. This is achieved by disabling JavaScript. In addition, the modified version of the browser successfully blocked the scripts necessary to collect information about your system.
If you'd like to try the Tor Browser Bundle and see how well it does at hiding your digital fingerprints, head over to the Tor website where you can download the bundle itself. And also get more information about how Tor helps you achieve anonymity and security when working on the Internet.
HMA VPN
This is an impressive VPN service from the UK that allows the user to hide their IP addresses, unblock some sites, geo-restricted channels and anonymously visit sites through one of the company's over 50 thousand private and anonymous IP addresses:
HMA's 934 VPN servers are located in 190 countries, using OpenVPN, PPTP and L2TP protocols. It is useful and easy to use software. All you have to do is subscribe to one of tariff plans: £7.99 for one month, £5.99 per month for six months or £4.99 per month for a year. After this, you need to install the software, enter your username and password and connect to the service.
All the hard work and configuration VPN for online anonymity Internet is provided automatically. In addition, a special built-in function “ Speed Guide" will automatically select the fastest VPN server based on your current location and connection.
The software is available for Windows, Mac and Linux. After you have registered an account and paid for the selected tariff plan, you can download the necessary software through the HMA control panel:
Manager software The VPN includes some interesting features, one of which is the connection speed review. You can also choose which VPN protocol you want to use. One of the most popular and fastest protocols is OpenVPN. In addition, you can set the parameters to change the IP address randomly every few minutes.
The program contains a convenient function " Secure IP Bind", which prevents applications from connecting to the Internet when HMA VPN is not running. You can choose your own country-specific VPN server and adjust the load ratio to connect to the VPN server with the fewest users and get more resources at your disposal.
CyberGhost
VPN, which is rightfully considered one of the best methods of anonymity on the Internet. CyberGhost 5.5 was recently introduced, which includes a number of additional benefits available in the paid package. Hiding your IP address and encrypting your connection is the norm for the CyberGhost team, but they feel they can do even more for you:
New features include Ad-Blocker, anti-virus protection malware and viruses, data compression, tracking prevention, forced transition to HTTPS, as well as access through the fastest servers.
The data compression feature increases the speed of your mobile connection, and also identifies and actively removes any content that helps collect information about the resources you visit.
Forced transition to HTTPS is useful function which many VPNs don't implement. By forcing a secure connection, you increase security of your work on the Internet and reduce the risk of your data being stolen:
In addition to new features, CyberGhost 5.5 features a faster and more user-friendly interface. Connections to servers located outside the UK are faster and overall download speeds are faster. The service also provides handy graphs that show how many cases of blocking, tracking, and forced switching to HTTPS occurred while using CyberGhost.
For getting additional information About, how to maintain anonymity on the Internet and the cost of various plans, visit the CyberGhost website.
Browser Add-ons
If reducing traffic isn't a big concern for you and you're only concerned about snooping, then use one of the many free add-ons available for IE, Chrome, and Firefox.
They can help block certain scripts and pop-ups, as well as identify elements that track your location.
DoNotTrackMe/Blur
Recently released, but already widely known, improved version of DoNotTrackPlus. Compared with previous versions Over 300 advertising platforms have been added to its blacklist, as well as more than 650 tracking technologies:
The add-on is available for Chrome, IE, Safari and Firefox. Once you install the extension and restart your browser, the DNTMe icon will appear in your toolbar and DoNotTrackMe will begin logging attempts to track your activity.
DNTMe works great in parallel with already installed add-ons. Your browsing experience will not be slowed down, and you will see the same content as before, except for some of the ad elements that are being tracked. You will receive information about the number of attempts made and blocked.
Adblock Plus
Another free add-on for IE, Chrome and Firefox. It is considered one of the best for ensuring anonymity on the Internet, blocks phishing and tracking, and protects you from malware and unwanted advertising:
You can add ready-made filters or use custom ones. But be careful when using unknown filter lists, as they may miss something important.
NoScript
Extension for Firefox, Seamonkey and other browsers from Mozilla. This is a free package with open source code, it blocks all JavaScript, Java, Flash and other unsafe plugins unless they are trusted. NoScript can be installed either through the Firefox Add-on Store or directly from the NoScript website:
NoScript does an excellent job of hiding information about your location and activity from scripts that request such data. The extension hides your digital " fingerprints» from the vast majority of sites on the Internet and provides decent level of anonymity and confidentiality.
Conclusion
Nowadays it is impossible to get complete anonymity on the Internet. This will require a secure VPN server, a variety of browser-based blocking methods, and special setting operating system.
However, by using one or a combination of several of the tools, packages and methods listed above, you can significantly increase your chances of remaining anonymous and out of sight of attackers tracking the activities of other people. In addition, you will protect yourself from a huge number of viruses, malware and spyware.
This publication is a translation of the article “ How to become anonymous online", prepared by the friendly project team
It happens in life that you need 100% anonymity when using the Internet through a browser (I’ll do without examples, otherwise tough guys will come to the comments again and accuse me of incitement and threaten me with department “K”). How to make sure that sites on the Internet (for example Google) cannot identify you and record information about any actions in your file?
It happens that you turn on a VPN with “incognito” mode, you don’t log in anywhere, and AdSense suddenly scares you with painfully familiar ads. How does he determine who is who?
To answer this question, let's conduct an experiment. Let's open tabs in four browsers:
- Tor Browser 6.0.2 (based on Mozilla Firefox 45.2.0);
- Safari 9.0 (incognito mode);
- Google Chrome 52.0.2743.82 (incognito mode);
- Mozilla Firefox 46.0.01 (incognito mode).
And let's see what data they can collect about a person. What do we tell the site about ourselves by typing the URL in the address bar?
We provide unique image rendering options (Canvas Fingerprinting)


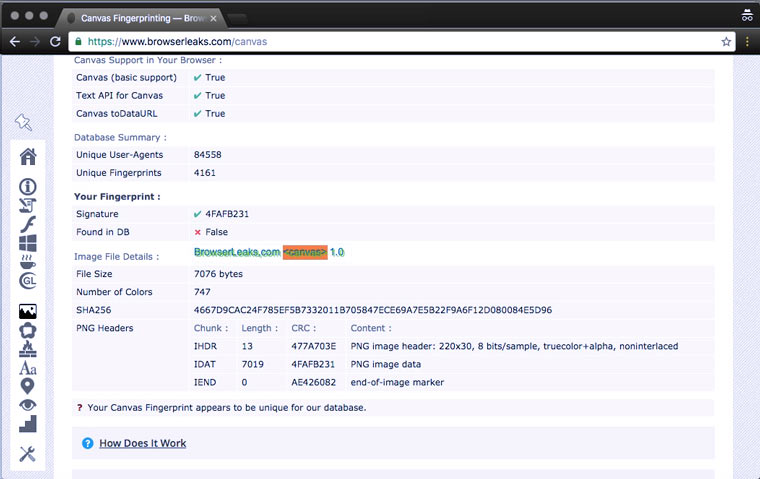

Canvas Fingerprinting is a user identification technology developed about 4 years ago at AddThis. The principle of its operation is based on the fact that when, when loading a page, a picture is drawn (rendered) (usually a single-color block in the background color with invisible text), the browser for this purpose collects a bunch of information about the system: what kind of hardware and graphics drivers, GPU version, OS settings, font information, anti-aliasing mechanisms and many other little things.
Together, this huge variety of details forms a unique characteristic that can distinguish a user's computer/browser combination from all others in the world. For each, it is written as a string similar to DA85E084. There are matches (according to Panopticlick, the average chance of finding a double is 1 in), but in this case, you can supplement them with other opportunities for identification (more on them below).
Tor asks permission to receive Canvas Fingerprinting, and if you are careful and do not give consent, you can keep this information to yourself. But all other browsers surrender their owner without a single peep.
You can read more about this identification method in Wikipedia.
We break through the database of advertising preferences




Many visited sites are now equipped with scripts for determining Canvas Fingerprint. Having received this unique value, one site can ask another for information about the person. For example, linked accounts, friends, IP addresses used and information about advertising preferences. Use the link below to check which systems have your consumer interests linked to Canvas Fingerprinting.
Tor again asked for the same permission as in the first point and, due to my refusal, nothing was found. Safari found me in 3 databases, Chrome in 13, and Firefox in 4. If you exit incognito mode, then in the latter the number of databases increases to 25, since most of them use good old cookies for identification.
We share the IP address and telecom operator




In Tor, you can change your “host country” using the New Identity button. And “incognito” modes do not hide your IP address (for this you must additionally use a proxy or VPN), but share your approximate location and information about your Internet provider with the site owners.
Revealing your city and the time in it (with geolocation services enabled)




On yandex.ru in Tor, without any location permissions, it showed where I was approximately and what time it was. It's the same with other browsers.
Send us your exact coordinates




Tor didn’t even ask permission to determine the coordinates and simply returned zeros. Safari, Chrome and Firefox asked for the standard resolution (as in normal mode) and did not bother to remind me that I was encrypted and should not reveal such data.
Revealing your city and the time in it (with geolocation services disabled)




Then I turned off location services on the Mac and went back to yandex.ru. Tor made the site think that I was in Romania, but left the time in Moscow (due to the mismatch of IP and time zone, it will be possible to ban VPN providers at once in the event of a ban). In other browsers everything remains the same.


The fact is that Yandex does not need GPS (or WPS data from the device) to determine location. After all, he has a “Locator”! Logged into the network via Wi-Fi? The access point is already in the database (see article). Did you give yourself internet from your phone? Cell tower will pass.
We provide information about language settings




Another sure sign of a VPN lover is that the language does not match the country whose IP he is using. Tor let me down - its language is always English (but it can be changed, but I thought it should change automatically depending on the country). The rest of the settings are the same as in normal mode.
We tell you everything about your browser and system




Operating system, connection speed, monitor color characteristics, support different technologies, browser window width, Flash version - a bunch of little things that complement the unique characteristics of the user. Tor manipulates some of this data (Windows 7 example), but other browsers are completely honest.
A person can change the IP, turn on “incognito”, and the script to raise prices will quickly calculate: “Who is this guy who is coming to us with a slow Internet, old version flash and Windows XP for the second time, but now you decide to pretend to be a resident of Seychelles? We’re increasing it by 20%!”
We share a list of installed plugins




Another characteristic that adds uniqueness to a person is the list of plugins (with version information) installed in his browser. Tor hides them. Other browsers do not.
As you can see, Tor Browser provides good anonymity. But historical facts suggest that if a person does something really serious using the onion network, then he will still be sometimes they find. Everyone probably remembers the revealing story with the founder of Silk Road (a drug store) Ross Ulbricht.
And “incognito” modes are only needed to surf on someone else’s computer and not leave traces. In addition to them, you can block JavaScript, this will reduce the number possible ways identification, but many sites will become unusable.
Open the list of fonts installed on the system (=> programs)

In addition to the experiment, I would like to talk about one more interesting function modern browsers. Any site can get a list of fonts installed on the system. Many applications have their own unique fonts, and by using them you can determine a person’s occupation. And based on this, show him advertisements. In Tor and incognito mode this does not work (or the list is too short).
All this is the tip of the iceberg
To protect against the above identification methods, there are special plugins for different browsers. But you shouldn't waste effort installing them. Since they cannot protect against the collection of all possible information.
After all, in the article I showed the simplest and most understandable examples of how browsers collect information about us. But there could be much more of them: flash cookies, Silverlight cookies, time lag behind the standard time (many have at least 0.2-0.8 seconds) - many little things that would be superfluous. After all, the reader already understands that by opening a browser, he communicates a huge amount of information about himself to the world and demonstrates a set of unique characteristics, which distinguishes his computer from all others.
What is the threat of all this information gathering?
You need to collect information about the majority of people on the planet for only one purpose - to increase the click-through rate of advertisements in order to earn more money from it. In principle, this is only beneficial - it is easier to find some goods or services.
More advanced identification methods are useful for stores to collect information about customers. So that a person cannot access the site under a different IP/disabling cookies and remain unrecognized. Language, time, rare font/plugin, monitor characteristics, a typical error in the search query you came from - and that’s it! Take off your skates, we recognize you. There is no doubt, this is the same person who placed order #2389 a year ago. With this data, automated marketing systems can sell him more.
Or, naturally, all this can be used by the intelligence services. But who knows how everything works there.
Not an easy task. It is a fact that we are being watched at every step. Here we are talking, in particular, about espionage for marketing purposes - companies collect information to create our profile and “effectively” select ads for us.
The desire for anonymity does not mean that we want to achieve any suspicious or illegal goals. But, if we send messages through the messenger and the entire conversation can be read by third parties, this is very annoying, because during a live conversation face to face, we also do not want anyone to eavesdrop on us.
Thanks to the programs from this package, you can use the Internet anonymously. Mozilla Firefox with the appropriate add-ons will provide us with security while surfing.
OpenVPN or Tor Browser Bundle programs will allow you to disguise our presence on the network. Temporary email addresses will protect you from spam. Finally, we will mention the Tails system, which works like a LiveCD and allows you to achieve much greater anonymity than any other system.
Opportunity secure anonymous connection to the Internet- a tempting offer. However, I recommend using it only when we want to use the services of a bank, post office or other services that use our personal data. The reason is simple - connection speed. If we establish an anonymous connection via VPN server, our signal may take a long time to circulate before reaching the selected server, which means slower page loading times.
Internet incognito - the best software
Try all the tools in the package and find out which one is best suited for which situation:
- I want to use a browser that doesn't spy on me:
Mozilla Firefox is a browser that cares about our privacy and has a special private mode.
- I need a browser add-on that will provide more protection:
HTTPS Everywhere And Privacy Badger are additives that will significantly increase our safety.
- I need anonymity and an encrypted connection to the Internet:
Tor Browser Bundle And OpenVPN– both will allow you to achieve your goal and they are completely free.
- I am interested in anonymous search for information on the Internet:
- I need a temporary email address:
There are many services that will provide relevant functionality, for example, Mailinator.
- I want to have my own secure cloud for files:
ownCloud provides the opportunity safe storage files on the Internet.
- I need secure messaging:
Signal And Telegram- examples of instant messengers that encrypt all your messages and ensure the security of information exchange.
- I want an operating system that provides anonymity on the Internet:
Tails- this is special operating system, in which all the tools that provide anonymity are installed by default.