In this tutorial, we will look at how to delete a Linux user along with his data and home directory.
If you System Administrator In a large company, most likely, deleting Linux users is a fairly common task for you. After an account becomes unnecessary or a user leaves the organization, his account should be deleted so as not to leave security holes.
When deleting Linux users, it is also important to delete their home directory to free up storage space for new users and their files. First, we'll look at how to delete a Linux user using the terminal, then we'll talk about how this is done in the graphical interface of one of the most popular distributions - Ubuntu.
To get some practice done in a real environment, let's create two users, losst and losst1, along with their home directories, and then delete them:
adduser loss
$ passwd lost
adduser losst1
$passwd losst1
Here the adduser command is used to create a user account and passwd to create a password.
Let's look at how to delete a Linux user in the terminal. To do this, use the command - deluser in debian and derivative systems, and in RedHat - userdel. Let's take a closer look at these two utilities.
Description of deluser
The deluser command syntax is very simple:
$deluser parameters user
The deluser command settings are located in the /etc/deluser.conf file; among other settings, it specifies what needs to be done with the user’s home folder and files.
You can view and change these settings by running the command:
vi /etc/deluser.conf
Let's take a closer look at these settings:
- REMOVE_HOME- delete the user's home directory
- REMOVE_ALL_FILES- delete all user files
- BACKUP- fulfill backup user files
- BACKUP_TO- backup folder
- ONLY_IF_EMPTY- delete a user group if it is empty.
These settings determine the default behavior of the utility when deleting a user; of course, they can be overridden using parameters for the command.
The following parameters are supported, they are similar to the settings, but there are more options:
- --system- delete only if it is a system user
- --backup- do backup copy user files
- --backup-to- folder for backups
- --remove-home- delete home folder
- --remove-all-files- delete all user files in the file system
Description of userdel
The userdel utility works a little differently, there is no settings file here, but there are options with which you can tell the utility what to do. The syntax is similar:
$ userdel parameters user
- -f, --force- forced deletion, even if the user is still logged in
- -r, --remove- delete the user's home directory and his files in the system.
- -Z- delete all SELinux objects for this user.
To remove a user from the server, it is better to use an advanced method, which we will consider below. When users use the server they run various programs and services. A user can be correctly deleted only if he is not logged in to the server and all programs running on his behalf are stopped, because programs can use various files belonging to the user, and this will prevent them from being deleted. Accordingly, then the user’s files will not be completely deleted and will remain to clog the system.
Blocking a user account
You can use the passwd utility to lock a user account. This will deny the user access to the system and prevent new processes from starting:
Run the passwd command with the --lock option:
passwd --lock loss
passwd: Password expiration information has been changed.
Kill all running user processes
Now let's find all the processes running as the user and kill them.
Let's find processes using pgrep:
You can see in more detail what these processes are by passing the pid of each of them to the ps command, like this:
ps -f --pid $(pgrep -u losst)
UID PID PPID C STIME TTY STAT TIME CMD
losst 14684 14676 0 22:15 pts/2 S 0:00 -bash
losst 14735 14684 0 22:15 pts/2 S+ 0:00 vi text
Now that you've made sure there's nothing important there, you can kill all processes using the killall command:
Killall -9 -u losst
The -9 option tells the program to send a SIGKILL termination signal to these processes, and -u specifies the username.
Based on Red Hat systems, to use killall you will need to install the psmisc package:
sudo yum install psmisc
Backing up user data
This is not at all necessary, but for a serious project it would not be a bad idea to create a backup copy of the user's files, especially if there might be important files there. To do this, you can use, for example, the tar utility:
tar jcvf /user-backups/losst-backup.tar.bz2 /home/losst
Deleting a user account
Now that everything is prepared, let's begin deleting the Linux user. Just in case, we’ll explicitly indicate that we need to delete the user’s files and home directory. For Debian:
deluser --remove-home losst
userdel --remove losst
If you need to remove all files belonging to a user on the system, use the --remove-all-files option, just be careful with it, as important files can be overwritten:
deluser --remove-all-files losst
The user is now completely removed, along with his files and home directory, from your system.
Removing a user in Ubuntu
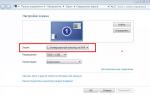
Open System parameters:
Open item Accounts:

As you can see, all actions are currently unavailable and are grayed out. To activate them, click the button unlock and enter the user password.
Now, in order to delete a user in Linux, just click on it with the mouse, and then click on the minus icon.
In the window that opens, you can choose what to do with the user files:

Naturally, only the home folder will be deleted, we are not talking about all files. And for correct removal, the user must not be working in the system.
conclusions
Deleting a user in Linux is not that difficult, regardless of where it needs to be done, on the server or home computer. Certainly, GUI more convenient, but the terminal, as always, offers more options. If you have any other ideas about this, please leave a comment!
Option -c - add a comment to the user
Option -g sudo - add a user to the sudo group.
The -s option will set the user's shell to /bin/bash
Option -d used to specify the user's home folder
Option -m will indicate that the folder needs to be created immediately:
Sudo useradd -c "Comment for user" -g sudo -d /home/NameUser -m -s /bin/bash NameUser
Set a password for the NameUser user:
Sudo passwd NameUser
Add a user using the adduser command
sudo useradd -c "Comment for user" -g sudo -d /home/NameUser -m -s /bin/bash NameUserEnter the password, answer all the questions asked, get a user with a password and home directory
Changing the user password
sudo passwd NameUserAdd a user to the sudo group
usermod -a -G sudo NameUserAdd a user/user group to Sudores directly:
Let's edit the file /etc/sudores.tmp editor visudo
Sudo visudo
Let's give root rights to the user named user_name
User_name ALL=(ALL:ALL) ALL
Let's give root rights to a group of users group_name by adding a line to the sudoers file -
Group_name ALL=(ALL:ALL) ALL
User and his groups
We look at the available groups on the host
Cat /etc/group
Checking the existence of the group examplegroup on the host where examplegroup is the group you are interested in
Grep examplegroup /etc/group
We check/find out which groups the user belongs to (as well as his uid, gid)
Id NameUser
Add an existing user NameUser to an existing group examplegroup
Usermod -g examplegroup NameUser
Removing an Ubuntu user
We use the command, the user's folder will not be deleted
Sudo userdel NameUser
Delete the folder if necessary
Sudo rm -r /home/NameUser/
We check whether the user has deleted; if there is no output, then the user has been deleted
Sudo grep -R NameUser /etc/passwd --color
List all local users
sudo cat /etc/passwd sudo cat /etc/shadowTo display more detailed information about the user, install the package finger
Sudo apt-get install finger
To view information about the user NameUser, run the command
Finger NameUser
To output information about all users to a file infoaboutalluser.txt let's create a script finger.sh
#!/bin/bash n=`cat /etc/passwd | cut -d: -f1` for i in $n; do echo "=========================================================================== ================ "finger $i done
Let's run the script finger.sh and save its contents to a file infoaboutalluser.txt
./finger.sh infoaboutalluser.txt
List all privileged users:
egrep ":0:0:" /etc/passwdor not privileged
Egrep -v ":0:0:" /etc/passwd
List all users whose names begin with the letters abcd:
Cat /etc/passwd | grep "^.*"
IN operating system Linux has many great security features, but one of the most important is the file permissions system. Linux, as a follower of the Linux kernel ideology, unlike Windows, was originally designed as a multi-user system, so file access rights in Linux are thought out very well.
And this is very important because local access to files for all programs and all users would allow viruses to easily destroy the system. But new users may find the new file permissions in Linux very confusing, which are very different from what we are used to seeing in Windows. In this article we will try to understand how file permissions work in Linux, as well as how to change and set them.
Initially, each file had three access parameters. Here they are:
- Reading- allows you to receive the contents of the file, but does not allow writing. For a directory, allows you to get a list of files and directories located in it;
- Record- allows you to write new data to a file or change existing ones, and also allows you to create and change files and directories;
- Performance- you can't execute a program if it doesn't have an execute flag. This attribute is set for all programs and scripts; it is with its help that the system can understand that this file needs to be run as a program.
But all these rights would be meaningless if they applied to all users at once. Therefore, each file has three user categories for which you can set different combinations of access rights:
- Owner- a set of rights for the owner of the file, the user who created it or is now set by its owner. Typically the owner has all rights, read, write and execute.
- Group- any user group that exists in the system and is associated with a file. But this can only be one group and is usually the owner's group, although another group can be assigned to the file.
- Rest- all users except the owner and users included in the file group.
It is with the help of these permission sets that file permissions are set in Linux. Each user can receive full access only to files that he is the owner of or to those that he is authorized to access. Only the Root user can work with all files, regardless of their permission set.
But over time, such a system became insufficient and several more flags were added that allow you to make files unchangeable or execute them as a superuser, we will look at them below:
Special file permissions in Linux
In order to allow ordinary users to execute programs on behalf of the superuser without knowing his password, such a thing as SUID and SGID bits was invented. Let's look at these powers in more detail.
- SUID- if this bit is set, then when the program is executed, the id of the user from whom it was launched is replaced by the id of the file owner. In effect, this allows regular users to run programs as superuser;
- SGID- this flag works in a similar way, the only difference is that the user is considered a member of the group that the file is associated with, rather than the groups to which he actually belongs. If the SGID flag is set on a directory, all files created in it will be associated with the directory's group, not the user's. This behavior is used to organize shared folders;
- Sticky-bit- this bit is also used to create shared folders. If it is installed, users can only create, read, and execute files, but cannot delete files owned by other users.
Now let's look at how to view and change file permissions in Linux.
How to view file permissions in Linux
Of course you can look up file permissions in Linux with file manager. They all support this feature, but this will give you incomplete information. For maximum detailed information For all flags, including special ones, you need to use the ls command with the -l parameter. All the files in the directory will be listed and all the attributes and bits will be shown there.
To find out the rights to a linux file, run the following command in the folder where the file is located:
Dashes are responsible for file permissions in Linux. The first is the file type, which is discussed in a separate article. Then there are groups of rights, first for the owner, for the group and for everyone else. There are only nine dashes for license and one for type.
Let's take a closer look at what the conditional values of the rights flags mean:
- --- - no rights at all;
- --x- only executing the file as a program is allowed, but not changing or reading;
- -w-- only writing and changing the file is allowed;
- -wx- modification and execution are allowed, but in the case of a directory, you cannot view its contents;
- r--- read-only rights;
- r-x- read and execute only, no write permission;
- rw-- read and write rights, but without execution;
- rwx- all rights;
- --s- SUID or SGID bit is set, the first is displayed in the field for the owner, the second for the group;
- --t- sticky-bit is installed, which means users cannot delete this file.
In our example, the file test1 has typical program permissions, the owner can do everything, the group can only read and execute, and everyone else can only execute. For test2, the SUID and SGID flags are additionally set. And for the test3 folder Sticky-bit is installed. The test4 file is available to everyone. Now you know how to view the rights to a linux file.
How to change file permissions in Linux
To change file permissions in Linux you can use the chmod utility. It allows you to change all flags, including special ones. Let's look at its syntax:
$ chmod options category action flag file
Options will not interest us now, except perhaps only one. With the -R option you can force the program to apply changes to all files and directories recursively.
- u- file owner;
- g- file group;
- o- other users.
The action can be one of two things, either add the “+” flag, or remove the “-” flag. As for the access rights themselves, they are similar to the output of the ls utility: r - read, w - write, x - execute, s - suid/sgid, depending on the category for which you set it, t - sets sticky-bit. For example, all users have full access to the file test5:
chmod ugo+rwx test5
Or we’ll take away all rights from the group and other users:
chmod go-rwx test5
Let's give the group the right to read and execute:
chmod g+rx test5
For other users read only:
For the test6 file, set the SUID:
And for test7 - SGID:
Let's see what happened:

As you can see, changing file permissions in Linux is very simple. In addition, you can change the basic rights using the file manager.
conclusions
That's all, now you know not only what file permissions are in Linux, but also how to view them, and even how to change them. This is a very important topic that beginners really need to understand in order to use their system more fully. If you have any questions, ask in the comments!
To conclude, I would like to offer a good video about access rights in Linux:
As the reader's response shows, the issue of separation of administrative rights in Ubuntu still remains unclear to most novice administrators, so we decided to bring some clarity to this issue with this material. Therefore, if you don’t know how su differs from sudo, where you hid root, etc., etc., it’s time to start studying our article.
Let's start with a small digression. The Linux administrative rights system goes back to the Unix OS and therefore has much in common with other Unix-like systems: BSD, Solaris, MacOS. At the same time, different distributions have their own implementation characteristics of certain aspects, so we will give specific examples regarding the Ubuntu family, but knowledge of the general rules will allow you to easily understand the environment of any other Unix-like OS.
The user has full administrative rights in Linux. root, whose rights cannot be limited, so everyday work on behalf of this user is extremely undesirable: careless actions of the user can lead to damage to the system, and compromising this account will give the attacker unlimited access to the system.
Therefore, a different scheme has been adopted in Linux: all users, including administrators, work under a limited account, and to perform administrative actions they use one of the rights escalation mechanisms. To do this, you can increase rights using the utility sudo or log in as superuser (root) without completing current session using the command su. Many people mistakenly confuse these two mechanisms, so let’s look at them in more detail.
Team su allows you to log in as another user (not necessarily root) without terminating the current session. So the command:
Su petrov
will allow you to log in as the user petrov, the user environment (home folder) will also be changed to belong to this user.
Team su allows you to log in under your account without specifying a username root"a. However this method has one significant drawback - to log in on behalf of another user you need to know his password. If you have several administrators, then each of them will know the superuser password and you will not be able to limit their rights.
In addition, it is unsafe; knowing the superuser password and the ability to log in under his name in case of compromise can lead to a complete loss of control over the system.
What happens if we try to increase rights in Ubuntu this way? We won't be able to do anything because we don't know the user's password root, at the same time, no one is stopping us from logging in as a different user.

"Wait!" - another user will say, “isn’t the first person getting root rights?” this user, which we specify during installation?" Indeed, administrative tasks can only be performed on behalf of the user created during installation; if we try to do this on behalf of another user, we will fail.
Here we come close to the second mechanism for increasing rights - the utility sudo. However, before moving on to studying it, it is worth clarifying: superuser (root) rights in Ubuntu belong to the root account, which is disabled by default. Therefore, increase permissions using the command su does not seem possible.
The main mechanism for elevating rights in Ubuntu is the utility sudo. This utility allows you to elevate rights to the superuser level for the command being executed, but you do not need to know the superuser password; the user must enter his own password. After which the utility will check whether this user has the right to execute this command on this host with superuser rights and, if the checks are successfully passed, will execute it.
It is important! The main difference su from sudo serves what su allows you to change current user to root, which requires an active superuser account in the system and knowledge of its password, sudo allows you to elevate rights for the command being executed without specifying a superuser password; the user must enter his own password; logging in as root with these credentials will not work.
Another important circumstance is that when using a pipeline or redirection with superuser rights, only the first part of the command will be executed, for example in the design:
Sudo command1 | team2
With root rights will only be executed team1. And the team
Sudo cat sources.list > /etc/apt/sources.list
will give an access rights error because the entry is in /etc/apt/sources.list will occur with normal user rights.
To perform complex combinations of commands, you can switch to superuser mode with the command
which is similar to elevating rights with a command su, however, this will not change the user environment and the current user’s directory will be used as the home directory, which is convenient and safe. Each administrator will only have access to their home directory.
Now is the time to figure out who has the right to use the opportunities sudo and to what extent. The file is responsible for the settings of this utility /etc/sudoers, despite the fact that this is a regular configuration file, to edit it it is highly recommended to use the command:
Sudo visudo
This command locks the file and checks the syntax, otherwise you risk losing administrative access to your PC due to a typo.
Syntax this file quite simple. For example, at the very end of the file there is an entry:
%admin ALL=(ALL) ALL
This means that the users of the group admin can execute any command on any host, on behalf of any user. As we can easily verify using the command groups in our case the user andrey belongs to the group admin, and the user petrov No.
But all the advantages of this utility lie in the ability to flexibly configure the parameters for obtaining rights in each specific case. For example:
Petrov ubuntu-lts=(andrey) ALL
This line allows the user petrov execute any command on the host ubuntu-lts on behalf of the user andrey. When specifying commands, you should indicate the full path to them; you can find it using the command which

For example, we want to allow users petrov And sidorov shut down and restart the computer, as well as remove tasks. However, these commands should not require entering a password.
Another nice feature of the sudo utility is the creation of aliases, so in our case we will add in /etc/sudoers the following lines:
User_Alias USERGROUP1 = petrov, sidorov
Cmnd_Alias CMDGROUP1 = /bin/kill, /sbin/reboot, /sbin/shutdown
With this we created two aliases USERGROUP1, where we included the users we need and CMDGROUP1 with a set of necessary commands, we can subsequently edit only aliases without affecting all the rules where they can be used. Then let's add a rule:
USERGROUP1 ALL = (ALL) NOPASSWD:СMDGROUP1
which will allow users listed in the specified alias to execute commands from the given alias on any host on behalf of any user without entering a password.
In addition to the above two, aliases are also available for the host name and users on whose behalf it is allowed to execute commands, for example:
Host_Alias WWW = webserver1, webserver2
Runas_Alias WWW = www-data, www-developer
USERGROUP1 WWW = (WWW) ALL
The given set of records will allow users entering USERGROUP1 execute any commands on behalf of users www-data And www-developer on the company's web servers.
Finally, let’s look at what to do if a root account is still needed. It's simple, to enable it, just set a password:
Sudo passwd root
Block again account superuser can be created with the command:
Sudo passwd -l root
Remember that all administrative tasks in Ubuntu can be done using the sudo utility, so don't enable the root account unless absolutely necessary!
As you can see, Ubuntu has rich administrative rights management capabilities, which allows you to flexibly distribute rights among several administrators, as well as give the ability to increase rights for some users, and do this efficiently and securely.