Just recently I needed to install a clean system on my computer to test the operation of some drivers. Honestly, I started by looking for a way to deploy a ready-made system on a flash drive and boot from it. I’ll tell you that’s another task. Nevertheless, in the process I managed to gain some great experience in this matter, which I am happy to share with you. Moreover, in a hacker’s arsenal there should be a multi-boot flash drive with all the necessary tools.

A multiboot drive helps to check hardware, prepare computers for OS installation, backup data and remove any malware. And also break passwords and delve into the system to your heart's content.
When the BIOS introduced the option to boot from USB drives, hackers' lives changed forever. Since then, with the help of a tiny device, you can do anything on any computer without opening its case and without attracting attention. You can gain complete control over the system only by going beyond its boundaries.
Today, almost any operating system can boot from a flash drive. Many operating systems generally create a layer of hardware abstractions HAL directly during installation or test installation on a RAM drive. Starting with Windows XP, a convenient preinstallation environment is available - WinPE. Now it has reached version 5.1 and is based on Windows Kits 8.1 Update. After some modifications, WinPE allows you to do almost everything that you can do installed Windows. For example, install drivers not only during the boot process, but also after it.
Adherents of the “old school” will certainly appreciate FreeDOS. She is quite omnivorous - any x86 platform will suit her. Even a browser and media player are available in this operating system. Modern Linux distributions easy to launch in Live mode, and some even have the function of saving changes after a reboot - USB persistence. Many data recovery programs and antivirus protection They themselves create images of boot disks that can be placed on a flash drive. In short, the choice of components for multibooting is very large.
By booting into WinPE mode, you can use the appropriate utilities to change the installed OS Windows passwords, system files and registry settings that are locked even for the administrator. Systems with end-to-end encryption and additional protection cannot be overcome so easily, but an ordinary home or office computer- easily. Individual programs allow you to gain complete control over the hardware, which is also impossible under normal conditions due to restrictions at the level of rights, drivers and services. This whole set
Tools are often written to different media because they have different requirements and conflict with each other, but there are ways to combine many of them into a universal assembly. This is what we will do.
We will need:
flash drive with a capacity of 8 GB or more;
GRUB bootloader;
a set of images with the desired programs and operating systems;
WinContig utility;
WinSetupFromUSB program (optional).
HOW TO CHOOSE A FLASH DRIVE FROM THE AVAILABLE
You can find out for sure what is inside a particular flash drive only after purchase. The iFlash database and utilities for identification by VID/PID help you avoid opening its case. Among many analogues, the free Flash Drive Information Extractor utility produced by ANTSpec Software is the only one that works correctly with USB 3.0 and new controllers.

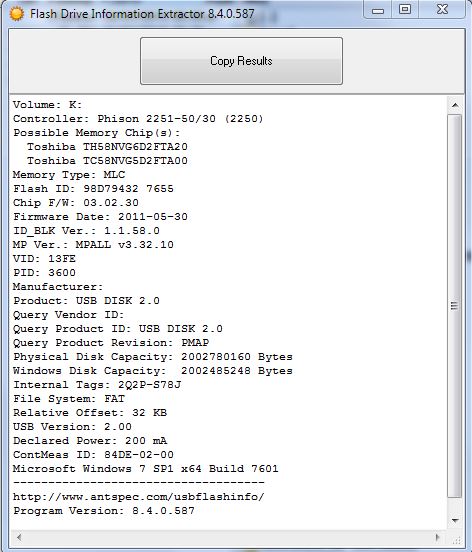
Each rewrite reduces the memory resource, so it is better not to use models with TLC chips. Modern NAND MLC chips are divided into two resource classes: 3K (up to 3000 rewrite cycles) and 5K (up to 5000 rewrite cycles). The latter are installed in expensive SSDs, and it is unlikely to find such a chip inside a flash drive. SLC memory with a resource of up to one hundred thousand cycles is now available only for enterprise-class SSDs and hybrid drive buffers. Flash drives with such memory stopped being made many years ago.
The Flash Drive Information Extractor window displays the type of memory chips, their estimated manufacturer and maximum current. From it you can judge the power consumption, and therefore predict the degree of heating of the flash drive and its ability to work for a long time in problematic conditions. At the dawn of USB-Flash production, they were equipped with a high-quality thermal interface, a power stabilization circuit, protection against interference and even polarity reversal. Modern models, as a rule, are completely defenseless. Now flash drives are not high technology, but consumables.
GRUB - GRAND UNIFIED BOOTLOADER
The GRUB boot loader is far from the only one, but it is a very convenient option for creating a multi-boot. It is universal, supports both old and all modern technologies downloads. In addition, the command syntax for other boot loaders (in particular, Syslinux) is easily rewritten into GRUB menu lines.
Today it is extremely easy to turn a flash drive into a multiboot one - manual operations are reduced to a minimum, there are many ready-made utilities, proven techniques, and support for new file systems has long been implemented. If there is no need to work with a clean DOS environment and old programs directly on the flash drive section, then you can safely format it to NTFS.

For Windows installations 8, 8.1, 10 and some other operations are generally required condition. Initially, all flash drives are sold with a FAT32 partition. The GRUB installer itself can create an NTFS partition - the main thing is not to make a mistake when choosing a disk. First you need to clear the flash drive by copying all the data to another medium. Now all that remains is to select it from the list in the Grub4DOS USB Installer window and click “Install”. After a few seconds, all operations will be completed, which will be confirmed by the menu.lst file in the root of the flash drive. This is just an example of a menu that we will be editing soon.
WE CREATE A SET
Before starting work, I advise you to Install GRUB on a USB flash drive with one click, read the entire article and download everything you need in advance using the links indicated in the text. Each of them
was tested, as was the multiboot procedure. Let's start with something simple: download the diagnostic program random access memory MemTest86 Free (for details, see the article ""). It is advisable to place it at the top of the list of the future menu, since the first item is selected automatically after a few seconds. If you miss a moment, you can simply press Esc, avoiding the long wait for something heavier to load. For modern computers with DDR4 you will need version 6.1.0 or later. It also includes release 4.3.7, which will automatically load when old memory types are detected.
title MemTest86 v.6.1.0 map /img/MemTest86-610.iso (0xFF) map --mem /img/MemTest86-610.iso (0xFF) map --hook chainloader (0xFF)
title MemTest86 v . 6.1.0 map/img/MemTest86 - 610.iso (0xFF) map --mem/img/MemTest86 - 610.iso (0xFF) map -- hook chainloader(0xFF) |
title MemTest86+ v.5.01 map /img/MemTest86p-501.iso (0xFF) map --mem /img/MemTest86p-501.iso (0xFF) map --hook chainloader (0xFF)
title MemTest86 + v . 5.01 map/img/MemTest86p - 501.iso (0xFF) map --mem/img/MemTest86p - 501.iso (0xFF) map -- hook chainloader(0xFF) |
Only the name and link to the image change, but not all ISOs can be loaded like this simple method. But, in addition to ISO, you can put images in IMA format on a flash drive. For the sake of experimentation, we’ll add a set of utilities from Active@, among which there is a program for resetting the password of any account and unlocking accounts in Windows. In the WinPE environment, it works with Windows from version 2000 to 8.1 inclusive, as well as Windows Server(2000–2012). The DOS release is much older and officially only supports password reset in XP, although SAM files are sometimes found in more recent ones Windows versions. The utility is still downloaded as an ISO image, but inside it there is a file floppy_2.88.00.ima, which can be extracted, renamed and downloaded directly to save space. The method here is different - FDD emulation.
title Active@ toolkit with Password Changer find --set-root /IMG/active.ima map --mem /IMG/active.ima (fd0) map --hook chainloader (fd0)+1 rootnoverify (fd0)
title Active @ toolkit with Password Changer find -- set - root / IMG / active . ima map -- mem / IMG / active . ima(fd0) map -- hook chainloader(fd0) + 1 rootnoverify(fd0) |
 A set of Active@ utilities for DOS runs with NTFS
A set of Active@ utilities for DOS runs with NTFS
You can continue to feel nostalgic later in the FreeDOS environment, but now we will move on to more relevant things. We integrate a set of diagnostic and recovery tools into multiboot - . Software Assurance subscribers can create one using the Microsoft Desktop Optimization Pack, while others can ask an admin friend or find it on the Internet. Having received the image, simply open it and copy the ERDC directory to the root of the flash drive. Let's add the following lines to the menu:
title MS DaRT map --unmap=0:0xff map --unhook root (hd0,0) chainloader /ERDC/bootmgr
title MS DaRT map -- unmap = 0 : 0xff map -- unhook root(hd0, 0) chainloader/ERDC/bootmgr |
 Launch of Microsoft DaRT
Launch of Microsoft DaRT
An alternative option is to not unpack anything, but download versions of recovery disks for x86 and x64 systems directly from the images created on your computer:
title Win 7 x86 Recovery find --set-root /img/W7-x86-Repair.iso map /img/W7-x86-Repair.iso (hd32) map --hook root (hd32) chainloader (hd32) title Win 7 x64 Recovery find --set-root /img/W7-x64-Repair.iso map /img/W7-x64-Repair.iso (hd32) map --hook root (hd32) chainloader (hd32)
title Win 7 x86 Recovery find -- set - root / img / W7 - x86 - Repair . iso map / img / W7 - x86 - Repair . iso (hd32) map -- hook root(hd32) chainloader (hd32) title Win 7 x64 Recovery find -- set - root / img / W7 - x64 - Repair . iso map / img / W7 - x64 - Repair . iso (hd32) map -- hook root(hd32) chainloader (hd32) |

The unpacking method is more reliable and less demanding on the amount of RAM. The second method is more convenient and faster for integration.
Installing Windows from USB drives has its own characteristics. For Windows 7, just copy all the files from the image to a flash drive (for example, using UltraISO) and write a simple command in the GRUB menu:
title Windows 7 Setup root (hd0,0) chainloader /bootmgr boot
title Windows 7 Setup root(hd0, 0) chainloader/bootmgr boot |
Manual integration of several Windows installation distributions on one flash drive is a topic for a separate article, as is step-by-step creation of WinPE-based assemblies. Here we will take ready-made ones as an example and focus on the mode Live USB.
On next step Let's add the most universal tool - a WinPE-based assembly. Alkid Live CD is suitable for older computers, and Xemom1 is suitable for new ones. Of course, you can take others - the mechanism for loading them is standard. The main thing is to avoid conflicts at the level of common directory names and different versions files. For example, the BOOT directory is found in many assemblies, and EFI is needed for installation latest versions Windows.
Alkid Live CD integration takes place in three simple stages. First, unpack the files bootfont.bin and A386ntdetect.com, as well as the PLOP directory, from the image to the root of the flash drive. Then we copy the entire A386 and PROGRAMS directories to the flash drive, after which we rename A386 to miniNT. Add the following lines to the menu:
title Alkid Live USB Full find --set-root /MININT/setupldr.bin chainloader /MININT/setupldr.bin
title Alkid Live USB Full find -- set - root / MININT / setupldr . bin chainloader/MININT/setupldr. bin |

Adding assemblies based on the latest versions of WinPE occurs in a similar way. They always have a directory with WIM images, which must be copied entirely to the root of the flash drive. It will also contain bootloader BOOTMGR. We will call it through the menu.
title Win PE 5.0 (Xemom1, unpacked) find --set-root /W81X/bootmgr chainloader /W81X/bootmgr
title Win PE 5.0 (Xemom1, unpacked) find -- set - root/W81X/bootmgr chainloader/W81X/bootmgr |

PASSWORD BREAKER AND KALI LINUX
Locally installed GRUB itself has a rootkit function. It always loads before the operating system, executes a given set of commands, and then calls the standard OS loader or the one you specify for it.
Password reset is quick, but rough method. If you need to hide traces of penetration, you will have to work hard on the selection. To do this, in any case, you will need the SAM and SYSTEM files, which can be easily copied when booting from a flash drive with any operating system that understands NTFS. Elcomsoft utilities added to the WinPE build will help deal with BitLocker protection and other misunderstandings.
By recording two versions of WinPE on a flash drive, aimed at old (x86, BIOS, MBR) and new (x86-64, UEFI, GPT) computers, you will get a universal environment for running hacker software. You can edit without the restrictions of the installed system hosts file, replace drivers and libraries, and in the registry editor - remove startup commands of cunning Trojans or
add yours.
No matter how convenient WinPE is, a hacker still has a lot of problems that can only be solved in Linux. Since the second version, Kali Linux has a convenient tool for creating custom ISO images - with any packages, Xs and connecting scripts during the build process. As before, they can be launched from a flash drive in Live or Persistence mode. The documentation describes how to burn Kali to a separate flash drive, and we will add it to multiboot.
title Kali 2.0 Lite set ISO=/img/kali-linux-light-2.0-i386.iso partnew (hd0,3) 0x00 %ISO% map %ISO% (0xff) || map --mem %ISO% (0xff) map --mem --heads=0 --sectors-per-track=0 %ISO% (0xff) map --hook root (0xff) || rootnoverify (0xff) chainloader (0xff)
title Kali 2.0 Lite set ISO=/img/kali-linux-light-2.0-i386. iso partnew (hd0 , 3 ) 0x00 % ISO % map % ISO % (0xff ) || map -- mem % ISO % (0xff ) map -- mem -- heads = 0 -- sectors - per - track = 0 % ISO % (0xff ) map -- hook root(0xff) || rootnoverify(0xff) chainloader(0xff) |

ANTIVIRUS
Antivirus developers often offer free images your boot disks. They are needed primarily to get rid of malware that has already infected the installed OS. Previously, such images could simply be downloaded and added to a flash drive by calling them with the command map, then now the structure of boot disks has become much more complicated. To guarantee their operation, you have to create temporary file marks, read volume identifiers, and perform a bunch of checks. In addition, the computer's disk subsystem
can be complicated, and at the next stage the antivirus loader will be lost when shifting partitions.

Writing an image with an antivirus to a clean flash drive is usually done simply - a separate program from the developer’s website or some other universal utility, for example UNetbootin. Wherein manual addition multiboot antivirus requires good knowledge of GRUB, general programming skills and a series of tests. Therefore, we will use the WinSetupFromUSB utility, which does most of the routine operations automatically.
Here you need to decide: will you only use it or want to make a custom flash drive manually. Below I provide lines for manual integration, but if you are too lazy to figure it out, just add images sequentially through the utility. The order doesn't matter.
 Launching Kaspersky Rescue Disk from an NTFS partition on a multiboot flash drive
Launching Kaspersky Rescue Disk from an NTFS partition on a multiboot flash drive For example, let's take the Kaspersky Rescue Disk image. When integrating an image, it can be placed together with others (for us this is the img directory). Add the following lines to menu.lst:
title KAV Rescue Disk set /a dev=*0x8280&0xff root (%dev%,0) set ISO=/img/kav_rescue_10.iso map %ISO% (0xff) || map --heads=0 --sectors-per-track=0 %ISO% (0xff) set /a dev=*0x82a0&0xff debug 1 parttype (%dev%,3) | set check= debug off set check=%check:~-5.4% if “%check%”==”0x00” partnew (%dev%,3) 0 0 0 && partnew (%dev%,3) 0x00 % ISO% if not “%check%”==”0x00” echo Error! map --rehook root (0xff) chainloader (0xff)
Many people are interested in the question of which operating system is better for hacking. First I will say that almost every professional and expert uses for this Linux or Unix. Although some operations can be carried out from under Windows And MacOS, almost all the tools are designed specifically for Linux.
But there are some exceptions, like programs Cain and Abel, Havij,Zenmap And Metasploit, which have been developed or can be transferred to Windows.
Applications for Linux, which were developed under Linux and then ported to Windows may lose some features. In addition, some options that are built into Linux, not available in Windows. For this reason, hacker tools in most cases are designed ONLY for Linux.
In general, to become a highly skilled hacker, you need to master some skills in Linux, and also work with distributions such as BackTrack or Kali.
For those who have never used Linux, devoted to This is a collection of basics Linux with an emphasis on the skills needed for hacking. So, you need to run BackTrack or other distribution Linux.
Step 1: Launch Linux
After launch BackTrack and login as user " root", enter the command:
Bt>startx
The screen should look something like this.
Step 2: Opening a Terminal
To become an expert in Linux, you need to learn how to use the terminal. In various distributions Linux many things can be done simply by pointing and clicking, just like in Windows or MacOS, but a professional hacker must know how to use a terminal to run most tools.
So, you can open the terminal by clicking on its icon in the bottom panel. A picture similar to this should appear on the screen.
 Terminal in Linux similar to the command line in Windows, but it is much more powerful. Unlike the command line, in the terminal with Linux you can do EVERYTHING and control the system more accurately than in Windows.
Terminal in Linux similar to the command line in Windows, but it is much more powerful. Unlike the command line, in the terminal with Linux you can do EVERYTHING and control the system more accurately than in Windows.
It is important to remember that in Linux character case matters. That is, the command " Desktop" differs from " desktop", which is not the same as " DeskTop" For some newbies to Linux This is challenging and requires memorization.
Step 3: Familiarize yourself with the directory structure
Let's move on to the basics of working in Linux. Many beginners get confused about the file system structure Linux. In Linux, unlike Windows, the file system is not tied to physical memory on the disk, so there is no system disk c:\, as the root of the operating system Linux, but there is / .
The forward slash character ( / ) represents the root ( root) or the top of the file system hierarchy. All other directories (folders) are located lower in the structure, like folders and subfolders on a disk c:\.
To visualize the file system, look at the diagram below.
 It is important to have a basic understanding of file structure because you will often need to use the terminal to navigate file system without a tool, like Windows Explorer.
It is important to have a basic understanding of file structure because you will often need to use the terminal to navigate file system without a tool, like Windows Explorer.
There are several in this graphical representation important points, which you need to pay attention to.
Catalog /bin– This is the location where the binary files are located. Programs that allow Linux work.
/etc– this is the folder in which configuration files are stored. IN Linux almost everything is configured using text files configurations that are in /etc.
In the catalog /dev device files similar to drivers are placed in Windows.
/var– This is the location where log files and other files are stored.
Step 4: Using the pwd Command
Terminal in BackTrack by default opens in the user's directory home. As shown in the graph above, in the hierarchy this is one step below the root directory root. You can verify which directory the user is in by typing the command:
Bt > pwd
Team pwd derived from " present working directory" (English: "represent the working directory"), and it returns the value /root, which means the user is in his root directory(do not confuse it with the top of the system file structure).
 Team pwd It’s better to remember, as it will always help you find out where the user is located in the directory system.
Team pwd It’s better to remember, as it will always help you find out where the user is located in the directory system.
Step 5: Using the cd Command
You can change the directory using the command CD(from the English change directory, “change directory”). In this case, to go “higher” in the folder structure you need to type:
Bt > cd ..
Team CD followed by two dots ( .. ) says: "move up one level in the folder structure." note that command line changed, and when introduced pwd, Linux responds that current user is in " / "or the top of the directory system (at the root directory of the system).
Bt > pwd
Step 6: Using the whoami command
The last step of this tutorial post will use the command whoami. The result of this command will be the output of the username that is logged into the system. Since the login here is made by the root user, you can log in account any user and the name of this user will be displayed in the terminal.
Bt > whoami
 That's all for now. IN the following training posts outlines the basics of work in Linux, which you will need to become a professional hacker.
That's all for now. IN the following training posts outlines the basics of work in Linux, which you will need to become a professional hacker.
Among the great variety of Linux distributions, there are projects designed to ensure the protection of personal data, the privacy of Internet surfing and the security of correspondence. Some of them can be installed on HDD, but they are mainly designed to run from Live CD/Live USB. This is useful when you need to quickly deploy an environment for private work on someone else's computer. Gentleman's set Such distributions usually include:
- Tor - you can’t go anywhere without it;
- I2P - anonymous Internet;
- means of encrypting IM correspondence.
Many of these distributions are built on top of Hardened Gentoo because it includes advanced exploit protections such as PaX and is lightweight on system resources.
Tails
Developer: Tails Web: https://tails.boum.org License: GNU GPL System requirements: PC with USB/DVD, 1 GB RAM Interface Russification: yes Security 9/10 Functionality 9/10 Ease of use 10/10Tails stands for The Amnesic Incognito Live System, it is a descendant of Incognito Linux, but unlike its progenitor, it is based on Debian. Main features of version 0.19:
- kernel 3.9.1;
- GNOME 2;
- Tor/I2P;
- the browser is configured with SSL by default, all traffic goes through Tor, unsecure connections must be installed in the Unsafe Web Browser.
There is also an interesting feature - disguise as Windows XP. Of course, it won’t hide it from a close eye, but it’s quite enough for an Internet cafe. When the work is completed, the contents of the memory are overwritten with zeros.
Liberte Linux
Developer: Maxim Kammerer Web: dee.su License: GNU GPL System requirements: PC with USB/DVD, 1 GB RAM Interface Russification: yes Security 10/10 Functionality 8/10 Ease of use 7/10Liberte is based on Gentoo, more precisely, on its Hardened version. Accordingly, protection against exploits is enabled by default. Software list:
- kernel 3.4.7;
- LXDE/Openbox;
- Florence virtual keyboard.
Unfortunately, there is no convenient interface to I2P. One of the highlights of the distribution is Cables communication, which allows you to anonymously exchange messages like Email. For this we use the same mail client, as for regular mail, - Claws-Mail. RAM cleaning is organized in the same way as in Tails. To be precise, this feature first appeared here, and Tails picked up the idea and implemented it at home.

Tin Hat
Developer: D’Youville College Web: License: GNU GPL System requirements: PC with USB/DVD, 4 GB RAM Interface Russification: no Security 10/10 Functionality 8/10 Ease of use 8/10The basic idea of this distribution, again based on Hardened Gentoo, is to use tmpfs wherever possible - which is why it is so memory-intensive. It boots from DVD, but is not a Live distribution in the modern sense of the word - when loading, it loads the entire root file system into memory, which, of course, takes a significant amount of time (about five minutes), and even encrypts it at the same time. Thus, although the key is physically stored in the same memory, it still needs to be found, and this requires special equipment. If you need to save data, loop-aes is used to encrypt it, since when using it it is almost impossible to distinguish encrypted data from random noise (of course, one cannot ignore that the same NSA, according to rumors, has more capabilities for cryptanalysis). The kernel in Tin Hat is completely monolithic, which significantly reduces the possibility of implementation malicious code to the zero ring.

Whonix
Developer: whonix.org Web: License: GNU GPL System requirements: PC with VirtualBox installed, 2 GB RAM, 10 GB disk space Russification of the interface: no, but you can install the appropriate packages Security 9/10 Functionality 8/10 Ease of use 7/10What makes Whonix different from others? anonymous distributions- dividing it into two parts: Whonix-Gateway and Whonix-Workstation. The first allows you to anonymize all traffic going to or from the second. This avoids many leaks, such as real IP leakage through Skype/Thunderbird/Flash applications, for the simple reason that the real IP is not available to them. Windows torification is also supported - as, indeed, any other OS; however, for greater anonymity, it is recommended to use Whonix-Workstation. Both parts are based on Debian, so there should be no problems with setup. KDE is used as the desktop.

JonDo Live-CD/DVD
Developer: JonDos GmbH Web: bit.ly/UpSh9Y License: GNU GPL System requirements: PC with DVD/USB, 1 GB RAM Interface Russification: no Security 9/10 Functionality 8/10 Ease of use 7/10This Live distribution, based on Debian and Xfce, contains two interesting features:
- Anonymizer JonDonym, which acts similarly to Tor. A premium account is paid, there are not so many exit nodes. The only advantage of paid accounts compared to Tor is the stated speed.
- MixMaster is software that allows you to send email anonymously. Briefly, the principle of its operation is as follows: the letter is sent to the final addressee not directly, but through a remailer; their cascade is also possible.
The Live DVD has LibreOffice, Gimp and more.
LiPoSe (LPS)
Developer: US DoD Web: www.spi.dod.mil/lipose.htm License: closed System requirements: PC with USB/DVD, 1 GB RAM Interface Russification: no Security 7/10 Functionality 8/10 Ease of use 8/10This distribution does not quite fit into the review - it was developed by the US Department of Defense for its needs. Nevertheless, it is of some interest. The purpose of its development is to create a safe environment for communications. There are three versions of this distribution:
- LPS-Public includes Firefox with Flash player, Java, and smart card support (CAC and PIY) for US officials to access sensitive government sites from home or while on vacation;
- LPS-Public Deluxe includes, in addition to the listed software, LibreOffice and Adobe Reader for working with documents containing a digital signature;
- LPS-Remote Access is intended primarily for internal use. Apparently it includes a VPN client. Unlike the first two, it is not available for free download.
I would like to emphasize once again that these distributions are not intended for anonymous surfing. Rather, they are designed for secure online banking.

FreedomBox
Developer: FreedomBox Foundation Web: freedomboxfoundation.org License: GNU GPL System requirements: Plug-computer (for example, Raspberry Pi) Russification of the interface: no Security 8/10 Functionality 6/10 Ease of use 5/10This is quite a promising development. Her idea is to create a mini-server that can be easily carried in your pocket. This mini-server will have software installed that allows, for example, to create a mesh network connecting several such devices. According to the developers, this should allow the creation of a “free cloud”. However, FreedomBox is also aimed at bypassing censorship in those countries where it exists or will soon appear. However, not everything is so rosy. The project seems to be quietly stalling due to a lack of developers and little funding...
If you want to start a career in the field information security or you are already working as a professional in this field, or you are simply interested in this particular area of knowledge, we will find a decent Linux distribution that suits your purpose.
There are countless Linux distributions for different purposes. Some of them are designed to solve specific issues, others provide a rich selection of different interfaces.
Today we will see linux distributions for hacking, some of the best, as well as for testing and penetration. Basically, various distributions with a focus on security are listed here. These Linux distributions provide various tools that are required for assessing network security and other such tasks.
Kali Linux is the most widely known Linux distribution for "ethical hacking" with penetration testing capabilities. Known as a Linux distribution for security testing, Kali Linux was designed with offensive security in mind and Kali Linux's predecessor along the way was BackTrack, which was built on top of several Linux distributions.
Kali Linux is based on Debian. It comes with a large number of tools for penetration testing in various areas of security and analysis. It now follows a rolling release model, which means every tool in your distribution will always be up to date.
Linux distributions for hacking are varied and feature-rich, with Kali Linux being perhaps the most advanced penetration testing platform. The distribution supports a wide range of devices and hardware platforms. Additionally, Kali Linux provides a decent set of documentation, as well as a large and active community.
BACKBOX
BackBox is a linux hacking distribution based on Ubuntu designed for penetration testing and security assessment. This is one of the best distributions in its field.
BackBox has its own own storage software, providing the latest stable versions of various network analysis toolkits and the most popular applications for "ethical hacking". It is designed with a focus on minimalism and uses the XFCE desktop environment. It provides a fast, efficient, customizable and rich experience. BackBox also has a whole community ready to help with any questions.

PARROT SECURITY OS
Parrot Security OS is a Linux for security testing and a relatively new player in this field. Frozenbox Network is behind the development of this distribution. The target audience of Parrot Security OS is penetration testers of various systems who need a friendly environment with online anonymity, as well as an encrypted system.
Parrot Security OS is based on Debian and uses MATE as its desktop environment. Almost every known penetration testing tool can be found here, along with some exclusive custom tools from the Frozenbox Network. And yes, it is available as a rolling release.

BLACKARCH
BlackArch is a linux hacking, penetration testing and security research distribution built on top of Arch Linux.
BlackArch has its own repository containing thousands of tools organized into various categories and the list is growing every day.
If you're already an Arch Linux user, you can customize the tools found in the BlackArch collection.

DEFT LINUX
DEFT Linux is a distribution created for computer analysis to run the system (LiveCD) to determine damaged or corrupted devices connected to the computer that are launched during boot.
DEFT paired with DART ( Digital Advanced Response Toolkit is a computer analysis system for Windows. It uses the LXDE desktop environment and the WINE application to run Windows tools.

Samurai Web Testing Framework
This tool is designed for the sole purpose of Internet penetration testing. Another difference from other distributions is that here we are talking about virtual machine, supported by Virtualbox and VMWare.
Samurai Web Testing Framework is based on Ubuntu and contains the best free and open source tools with a focus on website testing and attacking.
Samurai Web Testing Framework also includes pre-configured Wikis designed specifically for storing information during penetration tests.
PENTOO LINUX
Pentoo is based on Gentoo Linux. This distribution is focused on security and penetration testing, and is available as a LiveCD with stateful support (saving any changes made during a session to be available the next time you boot if you use a USB drive).
Pentoo - Gentoo with lots of customizable tools, kernel features and more. It uses the XFCE desktop environment. If you are already a Gentoo user, you can install Pentoo as an addition to your existing system.

CAINE
Caine- environment to assist in computer analysis, created as and entirely focused on a digital analysis project.
Caine comes with a rich set of tools designed specifically for system assessment and analysis. The project offers an excellent environment, which is organized with the aim of integrating existing software such as modular software and convenient GUI. The main objectives of the project that CAINE guarantees are: an environment that supports digital analysis during all four phases of the study, an intuitive graphical interface, unique working tools.

Network Security Toolkit
Network Security Toolkit - Linux security testing tool, is a bootable LiveCD based on Fedora. It provides security professionals and network administrators a wide range of open source network security tools.
Network Security Toolkit has an advanced web-based user interface for system/network administration, navigation, automation, network monitoring, analysis and configuration of many of the applications found in the Network Security Toolkit distribution.

Fedora Security Spin
Fedora Security Spin is a variant of Fedora designed for security auditing and testing, and can also be used for training.
The purpose of this distribution is to support students and teachers while they practice or learn methodologies in the fields of information security, web application security, computer analysis, peer review, and so on.

BUGTRAQ
Bugtraq is a Linux distribution with a huge range of hacking, analysis and other tools. If you're looking for Linux distributions to hack, Bugtraq is probably one of them.
Bugtraq is available with XFCE, GNOME and KDE desktop environments based on Ubuntu, Debian and OpenSUSE. It is also available in 11 different languages.
Bugtraq contains a huge arsenal of penetration testing tools - mobile analysis, research malware, along with tools specifically developed with the help of the Bugtraq community.

ARCHSTRIKE
ArchStrike (formerly known as ArchAssault) is a project based on Arch Linux for penetration testers and security professionals.
Hacking Linux distributions come with a wide range of software, as does ArchStrike, which comes equipped with all the best Arch Linux applications with additional penetration testing and cyber security tools. ArchStrike includes thousands of tools and applications, divided into groupings of packages by category.













