In files SYSTEM.DAT and USER.DAT in the catalog Windows 95/98 or in a folder C:\W\System32\Config\ V Windows NT The so-called system registry is stored, containing a large amount of information. In addition to the records required Windows Most programs also write their own information there when installed. To make changes to the registry, you need to open it using a program designed for this. An example would be the program REGEDIT, supplied as standard Windows. To launch it, open the dialog box Start/Run, enter Regedit and press OK.
You will see a window divided into two parts. On the left there is a navigator, similar to the Explorer navigator, and on the right is the actual information. The register consists of six sections: HKEY_CLASSES_ROOT, HKEY_CURRENT_USER, HKEY_LOCAL_MACHINE, HKEY_USERS, HKEY_CURRENT_CONFIG And HKEY_DYN_DATA. Each section contains folders. If a folder or section has subfolders, there is a " icon to the left of that folder plus". When you click on it, this folder " unfolds", and the icon turns into " minus"by clicking on which it can be done again" collapse". If you click on the folder icon or its name, then in the right window a list of those parameters that are contained in this folder (but not in subfolders!) will appear. Each parameter consists of its name and value. For each parameter there is its own path, where you can find it. The path consists of the sequence of folders in which the setting is located, starting with the parent folder (this is one of the six main sections above). An example of such a path would be HKEY_CURRENT_CONFIG\Display\Settings, and the name of the parameter Resolution. When combined, these two values - the parameter and its path (often called an address) indicate a unique parameter. For example, to two various parameters there may be the same path, two parameters may have the same names, but lie in different folders and subfolders, but there cannot be two parameters with the same address and name. You can search the registry (using the menu, or using a keyboard shortcut CTRL + F).
By selecting the desired section (by clicking on the section icon or its name), you can create a parameter or subsection in it. To do this you need to use the menu Edit/Create. IN system registry Windows There are 3 types of parameters: string, binary, And DWORD. A string stores one string ( string), V binary - binary value, V DWORD- decimal or hexadecimal value. When creating a parameter, you must specify its name. Then, by double-clicking on it in the right window, you can enter a parameter value (or change an existing one).
If a tip says to set the value of a parameter, it means that you need to change the existing value of the parameter to the desired value, or, if there is no parameter with that name, create it and then change the contents.
At the end of the work, most changes must be closed. REGEDIT and restart the computer. Well, first of all, let's figure out what it is: the registry Windows. When we install or remove programs, change settings Windows We install new equipment, all this is recorded and recorded in the registry. You could say that the registry is the heart Windows. To view or edit the registry you need to run the program Regedit (Start - Run - Regedit). Physically, the registry is stored in the directory Windows (95/98) under names User.dat And System.dat. I’ll say right away if you don’t know what you want to change to 100% don’t change it, otherwise it’s worthless. Well, for those who still changed, I’ll give you a hint. Upon successful loading, Windows makes registry backups under names User.da0 And System.da0. We will use this. Of course, you can create your own backup copies just in case. If Windows does not load, then press and hold when loading Ctrl. How to appear the menu select " Command prompt only", go to the folder Windows ("CD C:\Windows") and type the command scanreg/restore(V Windows NT - rdisk). Now reboot and Windows should start. If there is no such program, then you will have to type in the command line from the folder Windows:
attrib -h -r -s system.dat
attrib -h -r -s system.da0
copy system.da0 system.dat
attrib -h -r -s user.dat
attrib -h -r -s user.da0
copy user.da0 user.dat
Well, now let's move directly to the registry.
1.)Open regedit, find the key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall.
Here you will find the complete list installed programs. If some programs no longer exist, delete unnecessary folders with their names (an incomplete list is displayed in " Control Panel - Add or Remove Programs").
2.) In the key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Run
there is a list of all programs that start at boot Windows. You can delete unnecessary program, or you can add. To do this you need to create String parameter, for the name you need to enter the name of the program, and as the parameter value, enter the path to the program. If there are several users on your computer, then the program lists may be here:
HKEY_USERS\.DEAFAULT\Software\Microsoft\Windows\CurrentVersion and
HKEY_USERS\(Username)\Software\Microsoft\Windows\CurrentVersion
3.) That's it, the warm-up is over, and we move on to Main menu.
To get rid of an item Favorites (Windows 98), go to the section
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ Policies\Explorer
and create here Binary parameter NoFavoritesMenu with meaning 01 00 00 00 . All! Now the Favorites item will no longer appear. Delete the created parameter or change its value to 00 00 00 00 to return the item to its place. You can get rid of other items in the same way:
Documentation- parameter NoRecentDocsMenu
Settings - NoSetFolders
Find - NoFind
Shutdown - NoClose
Ending the session... - NoLogOff.
You can also cancel the job right click mouse in the main menu, for this create there DWORD-parameter under name NoChangeStartMenu with meaning 1 . Ready! Well finishing touches. Like this post about which button to get started with? No? Then we create DWORD- parameter named NoStartBanner and meaning 1.
4.) Go to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Winlogon
and create LegalNoticeCaption string parameter. Enter "Chernobyl virus detected" as the value, create another string parameter LegalNoticeText with the value "Click "OK" and all data on the hard drive will be destroyed." Restart Windows and enjoy the results. In the first parameter we enter the title, and in the second - the text itself.
5.)Now you can change the clock in the lower right corner. Go to
HKEY_CURRENT_USER\Control Panel\International
and create a string parameter sTimeFormat
Its meaning" HH:mm", where HH is the hour, : is the separating sign, and mm is the minutes. A reboot is required for the changes to take effect. It’s fun to see how a friend will struggle to set the clock if HH and mm are swapped! Well, if you want to mess up really bad, then you need to do this: Hm:mH"mH;Hm, etc.
6.) To avoid arrows in the shortcut icons, find the key HKEY_CLASSES_ROOT\Piffile and remove the parameter IsShortcut, the same should be done in the folder Lnkfile. Restart your computer and enjoy the results.
7.) Path to installation files Windows 95/98 lies in
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup.
Change it and Windows will search setup files when adding components or changing system settings.
8.) To remove the “palm” from shared resources, just delete the value Default from the key
HKEY_CLASSES_ROOT\Network\SharingHandler
9.) You can also remove all icons from the desktop altogether. To do this, create in the key
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
DWORD value named " NoDesktop". Reboot and you will see the cleanest Desktop in the world.
10.) In order to hide disks in Explorer, go to
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
and create here Binary parameter With name " NoDrives".
The value will depend on which drives you want to hide:
Disk A- meaning 01 00 00 00
B - 02 00 00 00
C - 04 00 00 00
D - 08 00 00 00
E - 10 00 00 00
F - 20 00 00 00
If you want to hide several drives, you need to sum their values. But keep in mind that these numbers are hexadecimal. To calculate correctly, use the calculator ( Programs - standard - Calculator). Select from menu Calculator "View - Engineering"", then select "Hex" and calculate. For example, to hide drives C And D need to be plused 04 00 00 00 And 08 00 00 00 . Enter the parameter value 0C 00 00 00. To hide drives A And E need to be summed up 01 00 00 00 And 10 00 00 00, we get the result 11 00 00 00.
11.)Open Properties: Screen, here we cover some tabs. In the registry editor, find the section
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System
create here DWORD-parameter with name NoDispBackgroundPage and meaning 1 . Now tab Background will not be displayed. The remaining tabs are hidden with the following options:
NoDispAppearancePage - Appearance
NoDispScrSavPage - Screensaver
NoDispSettingPage - Setting.
12.) Now let’s make the point To open with... always appeared in the context menu. Let's find the key for this HKEY_CLASSES_ROOT\*\ and create a section in it shell(if it doesn't exist). Here we will create another section " openas"and there's more in it" command".Change the value" Default" on " C:\WINDOWS\rundll32.exe shell32.dll,OpenAs_RunDLL %1". Done, you can check.
13.)To change the drop speed Main menu go to the key
HKEY_CURRENT_USER\Control Panel\desktop
and create String parameter Menu Show Delay. Enter the delay time (in milliseconds) into the value and reboot.
14.) Now let's try point Open in Notepad place it in the context menu. Let's go to the section HKEY_CLASSES_ROOT\*\shell(If not, create one). Create a section " Open" and change Default on " Open in Notepad". Now create a partition " command" and change it Default on " notepad.exe %1". Ready.
15.) Now let's play with Internet Explorer"ohm. Want to change your browser wallpaper? Please. Enter the key
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar
and create String parameter "BackBitmap". And as a parameter, enter the path to the picture in the format Bmp and restart your browser. But that is not all.
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main
create a new one String parameter Window Title. In the value, enter what you want to see in the title after the page title, restart your browser and enjoy. The conductor will look exactly the same.
16.) If you want to admire a name or just a word after hours in Systray(bottom panel) then go to
HKEY_CURRENT_USER\Control Panel\International\
and create two string parameters: s1159 And s2359. Their value should be entered desired name. Limit - 8 letters.
17.) When you need to restart the registry, but you don’t want to reboot the machine, then in some cases the following will help: click Ctrl+Alt+Del, then select Explorer and the " Complete task". When asked to turn off the car, refuse, then press " Cancel task"in the next window, after which you will see how it disappeared and appeared" Task bar".
Not everything works in Windows 95
Registry recovery
You must be careful when working with the registry. Deleting any important data accidentally or out of ignorance can lead to disaster operating system. Then only restoring the last working copy can save the situation.
If you are going to experiment with the registry, first save the SYSTEM.DAT and USER.DAT files on disk. They are located in the directory where the operating system was installed and have the attributes "read-only" and "hidden". If the registry is seriously damaged, you can rewrite these files to the Windows directory, set the necessary attributes, and the registry will be as good as new. Just don’t try to restore these files when Windows is loaded, otherwise the system will completely shut down and only a complete reinstallation will save it! To restore these files, you must first reboot into DOS and then replace the damaged files with good ones.
But this is not the only data recovery option. The fact is that the operating system, upon each successful startup, saves a copy of the registry in a CAB file, which is written to the hidden SYSBCKUP directory of the Windows directory. By default, the last five copies are stored. This number can range from 0 to 99 and is set by the value of the MaxBackupCopies key in the scanreg.ini file in the Windows directory. True, you shouldn’t set the value too high, because... files take up a lot of space (one file is more than a megabyte in size).
To restore the registry from one of these backups, you need to reboot into DOS and run the command
A list of available registry backups will appear, sorted by the time they were created. After selection the required copy the data will be safely restored, and you will receive a register that corresponds to the state of affairs at the time of its creation.
But if you installed any programs or changed operating system settings between the last backup and the registry failure, then all this data will be lost forever. Do we need this? Definitely not! To create a backup copy of the registry at any time, use the command
which, if the check passes normally, will create a backup copy.
Another option for backing up and restoring the registry is to export the section or entire branch that you plan to change. This can be done in Regedite for Windows under the Registry menu. Select the desired section and click on the "Export registry file" item. After specifying the file name, the data of this section will be exported to it. The file has a REG extension. To import it into the registry, just double-click on it and the data will be transferred. True, this method of information recovery has one significant drawback: all deleted or changed records will be restored, but added records will not be deleted. That's why this method It’s more suitable if you are making some minor changes, and to roll back them without entering the old data again, you can use export/import.
In general, you need to work with the registry extremely carefully, but if you back it up periodically, then no problems should arise
Today we will try to get into the Windows registry from the back door, without using the standard WinAPI functions intended for this. What will this give us in the end? The ability to write and read from the registry directly, bypassing the restrictions set by the developers of antivirus solutions!
Looking ahead, I’ll note: this topic is interesting, but there’s a whole set of serious problems. Although who said that we can’t handle it? 🙂
What is a registry, or some lyrics
From the point of view of the Windows operating system, the registry is a unique storage room. This uniquely built hierarchical database stores settings, data, registration information and other crap about almost everything in the system, from programs to the settings of a specific user. Almost everything is stored in the registry. Despite the fact that some programs prefer to store their settings in ini-configs (especially programs written for Win 3.11 - Editor's note), Windows itself reads all the necessary information about itself from the registry. To be fair, we note that in *nix-like operating systems the system for storing settings in all kinds of configs still dominates.
When starting to work with the registry, newbie system administrators are scared by their senior comrades that incorrect setting and changing registry settings can completely crash the system with its subsequent reinstallation. And indeed it is.
For example, so-called recovery points are copies of the registry. They are widely used by users when various problems arise with both the operating system and software and hardware.
It must be said that 99% of the information about the Windows registry is a description of the main keys plus tips on how to work with them. But how does the operating system itself work with the registry? And can we emulate her actions? Let's speculate a little.
So what?
The registry is both strong and weak side Windows. Strength registry is that for developers software there is no need to manipulate a bunch of configs, as is, for example, implemented in niksa. The registry is also convenient for creators of COM components - the system automatically registers such a component in the registry and facilitates the task of its further use.
The weakness of the registry is that access to modification of sensitive areas of the registry allows any program written by some newly minted malware to control Windows. Just remember the most famous branch of the Windows registry, which allows you to launch programs at the start of the OS :).
If in Windows 98 the registry could be repaired by anyone who thought of it, then starting with Windows XP only users with an administrator account have access to the registry. In Vista+, access to the registry is protected by UAC. This is understandable.
It must be admitted that with the release of Win7, security concepts when working with the registry were revised in better side. For example, the key registry branch HKEY_LOCAL_MACHINE is protected. In general, an attempt to write something to it will be redirected to the corresponding HKEY_CURRENT_USER branch for current user.
Interface
To work with the registry directly, Windows offers the programmer a whole set of WinAPIs that should be familiar to any system developer - these are Reg* functions such as RegOpenKey, RegQueryValue, and so on. In the Win kernel these are NtOpenKey, NtQueryValueKey and a number of others. There is no particular point in describing them - all documentation on the proper use of these functions can be found on MSDN.
Here's something worth noting. To control user actions, antiviruses and proactive programs installed interceptions on the mentioned functions, both in the kernel and in usermode.
With the release of Win7 x64, the situation changed, and I already wrote about it once. Windows developers have decided to abandon the ability to intercept potentially dangerous functions in the Win kernel. Now the KeServiceDescriptorTable variable is no longer exported in x64, and PatchGuard won’t let you rewrite the required section of the code. There are, of course, sadomasochistic solutions to bypass these restrictions - but there will be more trouble than profit. Moreover, Microsoft offers convenient ObRegisterCallbacks for monitoring the registry.
INFO
There is very little information on the Internet about the structures that describe the main registry files. And almost all of them are in English. Basic knowledge can be found. In addition, it is well written about the registry in the systems engineer’s bible “ Internal organization Windows" from comrades M. Russinovich and D. Solomon.
And now - about the most interesting
But what is a registry really? If you look into the WINDOWSsystem32config folder, you can see several files there: system, software, security, SAM and several others.
These are registry files.
However, it would be unfair to talk about the registry simply as some combination of files loaded into memory. Much of what the registry contains is dynamic in nature, that is, a number of values are calculated at the stage of loading the system itself, primarily this concerns certain hardware parameters. For example, this is the registry subkey HKEY_DYN_DATA, the data of which is located in random access memory and remain there until the operating system shuts down. The same, by the way, can be said about the key subkey HKEY_LOCAL_MACHINE, which does not have its own corresponding file on the disk, but is actually formed from other registry files, such as software, system and others.
Thus, the registry from the inside can be very loosely called a “virtual combination of registry files.” After the system starts, these files are located both in the page file (paged pool) and in nonpaged memory (nonpaged).
Registry structure
In order to learn how to work with the registry directly, you cannot do without knowledge of its internal structure. In general, Microsoft has never disclosed the internal structure of the files that make up the registry because it poses a security risk. According to my observations, all available descriptions of the registry files and its structure (and, by the way, there are very few of them) are the results of the research of pioneer researchers. The most complete, in my opinion, such a “research” is possible, it belongs to comrade Peter Norris.
We will not go into details of the organization and structure of the registry now; this is a long, tedious matter and definitely does not fit into the scope of the article. It is important to understand here that the registry is a hierarchical tree-like structure, sometimes also said to be like a honeycomb.
And what to do with all this now?
I’ll disappoint you right away: you won’t be able to easily play tricks directly with the registry in user mode; the system will not allow you to do this, as is usually the case with files occupied by other processes. If you try to dodge it, you can only read such a “busy” file, and only if you guess the flags with which it was opened. Unfortunately, it will not be possible to write the information we are interested in to the “registry file”. By the way, the recording feature necessary information it can work in the registry if you write to the registry *.BAK files, they are definitely writable.
So, watch your hand :).
The first thing that might come to your bright mind is to open the registry file directly and write something there.
Theoretically, this can be done, for this you need, firstly, to be able to work with “busy” files (look for methods on the Internet) and, secondly, as I said above, you need to know internal structure registry files. This method is rather clumsy, but despite its nonsense, it is quite viable, although it is difficult to implement in practice (try experimenting with it yourself).
Here I will offer two methods that will help you cut the registry into small pieces.
The first way is that for the configuration manager (Configuration Manager, part of the operating system, if you don’t know), the registry is nothing more than a set of strictly defined structures in operating memory, which, as it turns out, are very easy to work with. What are these structures, you ask? HBASE_BLOCK, HHIVE, HBIN, HCELL, HMAP_ENTRY, HMAP_DIRECTORY, a bunch of CM_* structures used by the config manager to manage the registry. From the operating system's point of view, the registry is simply a set of regulated structures in RAM. For example, the signature “regf”, which defines a “registry file”, is a predefined constant:
Define HBASE_BLOCK_SIGNATURE 0x66676572 typedef struct _HBASE_BLOCK ( ULONG Signature; //0x66676572 ULONG Sequence1; ULONG Sequence2; LARGE_INTEGER TimeStamp; .... ) And here is the “regf” signature...
That is, the point of all this monologue of mine is that there is a great opportunity to manipulate the registry at the operating system level, but without using its standard tools. How is this possible? We simply emulate the actions of the operating system itself, exactly the way it itself works with the registry! It is important, as I already said, to understand that for the OS itself, the registry is nothing more than a set of corresponding structures in memory.
If we have access to registry files at the kernel level, then why are we worse than the OS itself to establish its order?
And here the most interesting question appears on the scene - how to find these same structures in memory? Right, regular funds There is no system for solving this issue, so you will have to get out of it in a cunning way.
Knowing what the structures look like, you need to remember that each file, the registry hive, has its own constant signature. For example, "regf" is 0x66676572. For a hive, the signature will be 0xBEE0BEE0. With memory access from the kernel, we can find these signatures in memory quite easily by simply scanning it. You can also scan the memory in search of the “CM10” signature - it is this that is assigned by the config manager to the swap memory block, which is allocated for the CMHIVE structure. I believe that once you find an element that interests us in your memory, you will figure out what to do with it next :).
How, for example, can you change the value of a registry cell? The value is stored in the CM_KEY_VALUE->Data field, so if you have a task to change any field in a specific registry key, look for the value there:
Typedef struct _CM_KEY_VALUE ( WORD Signature; // #define CM_KEY_VALUE_SIGNATURE 0x6B76 WORD NameLength; ULONG DataLength; ULONG Data; //<---------- данные ячейки будут здесь ULONG Type; WORD Flags; WORD Spare; WCHAR Name; } CM_KEY_VALUE, *PCM_KEY_VALUE;
The second option is a kind of modification of the first. If you know, there is one peculiarity when working with the registry - all changes, that is, “creating new keys / writing / deleting keys,” as a rule, take effect after the system is rebooted (well, or after the explorer is restarted, this is such a hack method). Before this, all changes seem to be in a suspended, “dirty” state. Moreover, when the system accesses the registry, it communicates with it through the file system cache. This is understandable - there can be hundreds of calls to the registry per second, therefore, it is unreasonable to rely on the speed of the file system; no amount of speed will save you. Therefore, the system works with the registry, as they say, virtually, through the file system cache. And here, in order to pull the guts of the registry into the light, you need to get into the cache! How this is done has already been described in tyrnets, including in.
Pro & Cons, or in lieu of conclusion
What can I say in the end? The variation on the theme of direct control over the registry offered to the reader in the article is exclusively experimental in nature. I don’t argue, it is a bit difficult for practical implementation, and many will say that it is better to use normal WinAPI functions designed to work with the registry - and they will be right in some ways. However, the lib implemented by die_hard in practice, based on the principles given in the article, will have truly thermonuclear power, beyond the control of either the servers or the operating system itself.
Then I'll finish. Happy compiling and may the Force be with you!
WWW
Mark Russinovich’s article about the registry “Inside the Registry” is a must-read; there was even a Russian translation. A wonderful tool for collecting registry information: http://goo.gl/iSSVy.
Perhaps each of you has heard the word “registry,” but few have asked the question “What is it,” but in vain. After all, the ability to edit the registry can save a lot of time, money, nerves and effort. How to launch the registry of the Windows 7 operating system, as well as the main methods of using it, are discussed in detail in this article.
First, you need to understand what exactly the registry is. To better understand this, imagine a notebook with some notes in a certain sequence. If all the sheets from this notebook are torn out and mixed, the information will remain the same, but it will be much more difficult to read. You will have to first find the page you need before reading it, and this is wasted time.
A similar situation occurred when using the Fat16 file system, which had serious performance problems. Then it was decided to introduce a register to organize information. Over time, the problems solved by the registry disappeared, but it was retained due to backward compatibility.
Windows Registry is a hierarchically built database of parameters and settings of installed programs.
Physically, all registry settings are recorded in files and scattered throughout the system. When the program starts, the registry finds the necessary parameters and operates on them. The more applications there are on computers, the more parameter files there are, and the more time it will take to find what you need. Therefore, the registry needs to be cleaned from time to time to maintain system performance.
There are two ways to launch the Windows 7 registry:
- Start → in the search bar write regedit → in the results found, open the file regedit.exe.
- Launch Explorer → go to the C:\Windows folder → look for the regedit.exe file and open it.
If you did everything correctly, the Registry Editor will open.

Editing the registry. Export Import
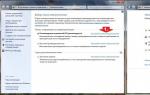
Before us is a window for editing the Windows 7 registry:
- On the left side there are sections.
- On the right are the parameters.
- At the bottom is the status bar, which displays the path to the parameter.
When working with registry settings, you need to be extremely careful and careful, because the registry is the nervous system of Windows. Therefore, before changing any settings, it is recommended to create a copy of the registry.
Right-click on the “Computer” section - Export - set a name, check the export range (should be “Entire Registry”) and specify the folder - click save.

After the above steps, a file with the extension .reg will appear. Now, if you mess up changing settings, the registry can always be returned to its original state.
To do this, click “File” – Import... - look for the Registry.reg we saved earlier and click “Open”. All parameters will return to the time the copy was created.

Recovering the administrator password using the registry
For an example showing what tasks can be performed in the registry, consider the following problem. Let's assume that you have forgotten your administrator profile password. No problem! It can be changed using the registry. To do this we need a Windows 7 installation disk.
- Boot from the installation disk. After copying the new data, we will be asked to select a language. Leave everything as it is and click “Next”.
- In the new window, select “ ”, after which the computer will search for installed operating systems.
- A window may appear with the text “Problems detected in the boot options.” Ignore and select the operating system and click “Next”.
- In the next window, select the lowest option “Command Line”

- At the command line, type the command we already know, regedit, and press Enter.
- In the editor, select HKEY_LOCAL_MACHINE
- Then, in the File menu, select “Load hive”.
- Go to the folder C:\Windows\System32\config (the letter may differ from the usual C). We are interested in the SYSTEM file.

- Enter any section name. For example: 888.
- Go to the HKEY_LOCAL_MACHINE\888\Setup section. Click twice on the parameter:
- CmdLine , enter cmd.exe and click OK
- SetupType , replace 0 with 2 and click OK.
As a result of the above manipulations, it should look like this:

The registry stores information about your computer's configuration, Windows settings, and settings for installed programs. System components continually access this information. Therefore, if a registry failure occurs, programs may stop working or partially lose their functionality. Let's take a closer look at the nuances of working with it.
Launching Registry Editor
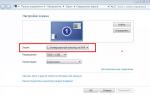
The easiest way to open the Registry Editor in Windows 7 is through the “ Execute" It starts in the menu " Start» or a combination of buttons Win + R. In the text line, enter the command regedit and complete it. 
It is worth understanding that editing system parameters can lead to computer malfunctions and the inability to launch some programs. Therefore, it is recommended that only experienced users make any changes. Inept actions can lead to serious consequences.
Problems Occurring
The installation process of almost any program or utility includes making changes to the registry. If the installation is carried out incorrectly, or a failure occurs during it, then there is a possibility of incorrect editing of system files. Sometimes this does not affect the performance of the computer in any way. But in some cases it leads to failures, slowdowns and other negative factors.
Problem solving
There are three large groups of problems associated with the registry: fragmentation, filling with unnecessary information, and data corruption. Everything is clear with the last category, let’s take a closer look at the other two.
The phenomenon of fragmentation is that a file is written in blocks to different areas of the drive. At the same time, the speed of access to it slows down. Registry data is also susceptible to fragmentation.
Most often, the program is not completely removed from the computer; residual data is sometimes not erased. These include entries in the registry. A large number of them leads to slowdown of Win 7.
In the first case, defragmentation will help; it is performed using the utility Defraggler. To solve the second problem it is worth installing CCleaner. And for the third - roll back the OS.
Problem 1: Fragmentation
Utility Defraggler designed to optimize work with registry data. With its help you can perform defragmentation.
Defragmentation is only available before the OS boots. Therefore, the utility will run when the computer starts. Follow the instructions to set it up:

Note: first system startup after setup Defraggler will last longer than usual. This is quite normal, because the computer takes a certain time to process the data. Subsequent downloads will be much faster.
When defragmentation is successful, the system will boot. But the program is configured in such a way that the procedure will be performed every time the computer starts. To disable this setting, remove Defraggler or change its operating parameters. But it is advisable to leave everything as it is at the moment. This will improve the speed of your PC after booting.
Problem 2: Residual files
An experienced user can clean the Windows 7 registry manually. But it is preferable to use special software for this. In this case, there is no risk of damaging important data.
It is worth highlighting CCleaner. This is a powerful utility for cleaning your Windows PC. It has many different functions, including cleaning registry data.
Operating instructions:

It is advisable to clean residual data regularly, constantly making backup files. It will come in handy if changes to the registry cause any problems in Windows 7.
Problem 3: Data Corruption
If any actions with changing registry settings lead to serious problems, then the previous methods will not help solve the problem. In this case, it is preferable to perform a registry repair in Windows 7.
The simplest option is rollback. In this case  The OS will return to its previous state, when no changes were made that caused the error.
The OS will return to its previous state, when no changes were made that caused the error.
Windows recovery instructions:

When choosing a restore point, you should focus on the date. Button " Find affected programs» will display system elements that will be removed during the rollback. 
default
sam
security
software
system
.During the download process, the system gains exclusive access to these files and, therefore, you cannot do anything with them using standard tools for working with files (open for viewing, copy, delete, rename). To work with the contents of the system registry, special software is used - registry editors (REGEDIT.EXE, REGEDT32.EXE), which are standard components of the operating system. To launch the registry use "Start" "Run" - regedit.exe
In the left half of the window you see a list root partitions (root keys)
registry Each root partition may include nested sections (subkeys)
And parameters (value entries).
Briefly about the purpose of root partitions:
HKEY_CLASSES_ROOT ( abbreviation HKCR) - Associations between applications and file extensions and information about registered COM and ActiveX objects.
HKEY_CURRENT_USER (HKCU)- Settings for the current user (desktop, network settings, applications). This section is a link to the HKEY_USERS\User Identifier (SID) section in the form S-1-5-21-854245398-1035525444-...
SID is a unique number that identifies a user, group, or computer account. It is assigned to the account when it is created. Internal Windows processes access accounts by their security codes rather than by user or group names. If you delete and then create an account again with the same username, the rights and permissions granted to the old account will not be preserved for the new account because their security codes will be different. The abbreviation SID is derived from Security ID. To view the correspondence between SID and username, you can use the PsGetSID.exe utility from the package
HKEY_LOCAL_MACHINE (HKLM)- Global hardware and software system settings. Applicable to all users. This is the largest and most important part of the registry. The main parameters of the system, hardware, and software are concentrated here.
HKEY_USERS(HKU)- individual environment settings for each system user (user profiles) and a default profile for newly created users.
HKEY_CURRENT_CONFIG (HKCC)- configuration for the current hardware profile. Usually there is only one profile, but it is possible to create several using “Control Panel” - “System” - “Hardware” - “Hardware Profiles”. In fact, HKCC is not a full-fledged registry key, but just a link to a key from HKLM
HKLM\System\CurrentControlSet\CurrentControlSet\Hardware Profiles\Current
The capabilities of a particular user when editing registry data are determined by his rights in the system. Further in the text, it is assumed, unless otherwise stated, that the user has system administrator rights.
Actually, in the root section of HKLM there are 2 more subsections named SAM and SECURITY, but access to them is allowed only under the Local System Account, under which system services are usually run. That is, to access them, you need the registry editor to be launched with Local System rights, for which you can use
psexec.exe -i -s regedit.exe
A detailed description of the utility is on the page "PSTools Utilities"
During the loading and operation of the operating system, registry data is constantly accessed for both reading and writing. Even one incorrect setting in the registry can lead to a system crash, as can the integrity of individual files. Therefore, before experimenting with the registry, take care of the possibility of saving and restoring it.
Saving and restoring the registry
1. Using Restore Points In Windows XP, there is a mechanism by which, if problems arise, you can restore the computer to its previous state without losing personal files (Microsoft Word documents, list of viewed pages, pictures, favorite files and e-mail messages). Restore Points are created automatically by the system when the computer is idle, as well as during significant system events (such as installing an application or driver). The user also has the ability to force them at any time. These restore points allow you to return the system to the state at which they were created.
To work with recovery points, use the \windows\system32\restore\rstrui.exe application ( Start - Programs - Accessories - System Tools - System Restore).

Recovery checkpoint data is stored in the directory System Volume Information system disk. This is a hidden system directory, access to which is allowed only to the local system account (Local System, i.e. “System Restore Service”). Therefore, if you want to access its contents, you will have to add your account rights using the "Security" tab in the properties of the "System Volume Information" directory. The System Volume Information folder has a subdirectory with a name starting with _restore... and inside it - subdirectories RP0, RP1...: - this is the data from recovery points (Restore Point - RPx). Inside the RPx folder there is a directory snapshot, containing copies of the registry files at the time the checkpoint was created. When you perform a system restore operation, core system files and registry files are restored. The mechanism is quite effective, but it can only be used in Windows itself. If the system is so damaged that loading is impossible, there is still a way out of the situation. How - read the article "Problems with loading the OS" section
2. Using the NTBACKUP.EXE backup/restore utility
Windows 2000 does not have a restore point mechanism. However, as in Windows XP, there is an archiving utility, or rather, backup and restore NTBACKUP.EXE, which allows you to do almost the same thing that is done when creating restore points (and even much more). NTBACKUP allows you to create an archive of the system state from 2 parts - a boot floppy disk, which allows you to perform recovery even on a non-bootable system, and the actual archive of data for recovery (in the form of a regular file with the .bkf extension, saved on your hard drive or removable media). To get a copy of the system state, click "Start" - "Run" - ntbackup.exe

We launch , and tell it that we need to archive the system state.

And where to store archive data

After completing the wizard, a system state archive will be created (D:\ntbackup.bkf) Using "Restoration Masters" you can always return the system state at the time the archive was created.
3. Using the utility for working with the registry from the command line REG.EXE
In Windows 2000, the REG.EXE utility is included in the Support tools package (you can also use REG.EXE from Windows XP - just copy it to the \winnt\system32 directory). Runs from the command line. When launched without parameters, it displays brief help on how to use it:
Program for editing the system registry from the command line, version 3.0
(C) Microsoft Corporation, 1981-2001. All rights reserved
REG Operation [Parameter List]
Operation == [ QUERY | ADD | DELETE | COPY |
SAVE | LOAD | UNLOAD | RESTORE |
COMPARE | EXPORT | IMPORT]
Return code: (except REG COMPARE)
0 - Successful
1 - With an error
To get help for a specific operation, enter:
REG Operation /?
Examples:
REG QUERY /?
REG ADD /?
REG DELETE /?
REG COPY /?
REG SAVE /?
REG RESTORE /?
REG LOAD /?
REG UNLOAD /?
REG COMPARE /?
REG EXPORT /?
REG IMPORT /?
To backup the registry use REG.EXE SAVE, to restore - REG.EXE RESTORE
For help
REG.EXE SAVE /?
REG SAVE section File name
Section - Full path to the registry key in the form: ROOT\Subkey
ROOT - Root section. Values: [ HKLM | HKCU | HKCR | HKU | HKCC].
subkey - Full path to the registry key in the selected root section.
File name - The name of the saved file on disk. If the path is not specified, the file
is created by the calling process in the current folder.
Examples:
REG SAVE HKLM\Software\MyCo\MyApp AppBkUp.hiv
Saves the MyApp section to the file AppBkUp.hiv in the current folder
The syntax of REG SAVE and REG RESTORE is the same and is quite clear from the help. There are, however, some points. In the Windows 2000 version of the utility, it was impossible to specify the path in the file name for saving a registry key and saving was performed only in the current directory. Help from the utility itself and examples of its use for saving (REG SAVE) can be used to save any registry keys, incl. HKLM\software, HKLM\system, etc. however, if you try to restore, for example, HKLM\system, you will receive an access error message due to the registry key being busy, and since it is always busy, restoring using REG RESTORE will fail.
To save the SYSTEM hive:
REG SAVE HKLM\SYSTEM system.hiv
To save a SOFTWARE hive:
REG SAVE HKLM\SOFTWARE software.hiv
To save the DEFAULT bush:
reg save HKU\.Default default.hiv
If the file exists, REG.EXE will throw an error and exit.
The saved files can be used to restore the registry by manually copying them to the %SystemRoot%\system32\config folder.
4. Manually copying registry files.
If you boot into another operating system, then you can do whatever you want with the files from the registry folder. If the system file is damaged, you can use, for example, the system.hiv file saved using REG SAVE, copying it to the registry folder and renaming it to system. Or perform the same action using a saved copy of the system file from the recovery checkpoint. This method of restoring the registry is described in some detail in the article "Problems with loading the OS"
5. Using the registry export-import mode.
The Registry Editor allows you to export both the entire registry and individual sections to a file with the extension reg Importing the reg file obtained during export allows you to restore the registry. Click on "Registry" -> "Export (Import) registry file". Import can also be done by double-clicking on the reg file shortcut.
6.Usage special utilities for working with third-party registries.
There are many third-party programs for working with the registry, which allow you not only to save and restore registry data, but also to perform a lot of other useful operations, such as diagnosing and deleting erroneous or unnecessary data, optimization, defragmentation, etc. Most of them are paid - jv16 Power Tools, Registry Mechanic, Super Utilities Pro Reg Organizer and others. List and brief description on secutiylab.ru
The main advantages of these programs include, as a rule, a simple user interface, the ability to perform fine tuning operating system and user preferences, cleaning from unnecessary entries, advanced capabilities for searching and replacing data, backup and recovery.
Perhaps the most popular software for working with the registry is jv16 Power Tools Macecraft Software Company. The main advantages are high reliability, versatility, simplicity and ease of use, support for several languages, incl. Russian. However, not everyone knows that there is also a free option called Power Tools Lite. Of course, it is far from a fully functional jv16, but it is quite suitable for searching data, cleaning and optimizing the registry. I note that the backup created by this program is just a reg file to restore the state of the registry before it was changed. Many (if not most) registry programs create similar copies, useful only for restoring the data they change. If the registry is damaged, they will not help you. Therefore, when choosing a (especially free) program with the ability to backup the registry, understand what copies it creates. The ideal option is a program that creates copies of all registry hives. If you have such a copy, you can always completely restore the registry by simply copying files. I would recommend the free console utility regsaver.exe Download, 380kb
Program website.
The utility saves registry files to the directory specified as a command line parameter:
regsaver.exe D:\regbackup
After executing the program, a subdirectory will be created in the D:\regbackup directory with a unique name consisting of the year, month, day and time of creation backup copy registry files ("yyyymmddhhmmss"). After completing the backup, the program can turn off the computer or put it into sleep mode:
regsaver.exe D:\regbackup /off /ask- Turn off computer. The /ask switch requires user confirmation when turning off the power.
regsaver.exe D:\regbackup /standby- Put to sleep mode without confirmation (no /ask)
regsaver.exe D:\regbackup /hibernate /ask- Switch to Hibernate mode
Instead of a standard shutdown of the computer, you can use a registry backup and shutdown when completed.
7. Restoring the registry in the absence of backup copies.
For example, when you boot the system, you see a message about the integrity of the SYSTEM registry hive:
Windows XP could not start because the following file is missing or corrupt: \WINDOWS\SYSTEM32\CONFIG\SYSTEM
If you did not back up the registry data, the mechanism for creating recovery checkpoints was disabled, or you used Win2K, where this mechanism simply does not exist, then there are still chances to revive the system by booting into another OS and restoring system file. Even if the contents of this file are not entirely up-to-date, the system will most likely remain operational. You may need to reinstall some software products or update drivers.
The Registry Editor allows you to open not only “your” registry files, but also files that are the registry of another operating system. In Windows 2000, the regedt32.exe editor was used to load a registry file (hive) saved on disk; in Windows XP, the regedt32.exe and regedit.exe functions were combined and, additionally, it became possible to restore a damaged hive during boot. For this
Boot into Windows XP ( Windows Live,Winternals ERD Commander, installed in another WinXP directory, another computer with the ability to load the problematic registry hive over the network or from external media). Launch Registry Editor.
On the left side of the registry tree, select one of the sections:
HKEY_USERS or HKEY_LOCAL_MACHINE.
On the menu Registry(In other versions of Registry Editor, this menu item may be called " File") select command "Load Hive".
Find the damaged bush (in our case - system).
Click the button Open.
In field Chapter Enter the name that will be assigned to the loaded hive. For example BadSystem.
After clicking OK a message will appear:

In the left window of the Registry Editor, select the mounted hive (BadSystem) and run the command "Unload bush". The damaged system will be restored. Moreover, the Windows XP Registry Editor will quite successfully restore the registry of the older Windows 2000 OS.
Registry monitoring.
One of best programs for registry monitoring, from my point of view, is RegMon Mark Russinovich - a small and functional utility that does not require installation and works in operating rooms Windows systems NT, 2000, XP, 2003, Windows 95, 98, Me and 64-bit Windows versions for x64 architecture. Download RegMon.exe v7.04, 700kb Regmon allows you to monitor in real time which applications access the registry, which sections, and what information they read or write. The information is presented in a convenient form that you can customize to suit your needs - exclude from the monitoring results data on working with the registry of applications that are not interesting to you, highlight with the selected color what you consider especially important, include only selected processes in the monitoring results. The program allows you to quickly and easily launch the Registry Editor and navigate to a specified section or parameter. It is possible to perform monitoring while the operating system is loading and recording the results in a special log, %SystemRoot\Regmon.log.
After starting RegMon, you can define filtering criteria for registry monitoring results:

By default, all registry access events are logged. The filter is specified by field values:
Include- If *
- perform monitoring for all processes. Process names are separated by ";"
. For example - FAR.EXE;Winlogon.exe- registry accesses will be recorded only for the far.exe and winlogon.exe processes.
Exclude- which processes to exclude from monitoring results.
Highlight- which processes are highlighted in the selected color (red by default).
The filter field values are remembered and displayed the next time Regmon is started. When the button is pressed Defaults The filter is reset to its default settings - record all accesses to the registry. It is more convenient to form filter field values not at the start of RegMon, but during the monitoring process, using the right-click menu for the selected process - Include process - include this process in monitoring, Exclude process - exclude this process from monitoring. After starting Regmon with default filters, you will see a large number of entries about access to the registry and, using Include/Exclude process, you can configure the output of only the results of the process(es) you need.

Purpose of the columns:
#
- number in order
Time- Time. The time format can be changed using the tab Options
Process- process name: process identifier (PID)
Request- request type. OpenKey - opening a registry key (subkey), CloseKey - closing, CreateKey - creating, QueryKey - checking the presence of a key and getting the number of nested keys (subkeys), EnumerateKey - getting a list of names of subkeys of the specified section, QueryValue - reading the value of a parameter, SetValue - write down the value.
Path- path in the registry.
Result- the result of the operation. SUCCESS - successful, NOT FOUND - key (parameter) not found. ACCESS DENIED - access is denied (insufficient rights). Sometimes there is a BUFFER OVERFLOW - buffer overflow - the result of the operation does not fit in the program buffer.
Other - Additional Information- the result of the executed request.
The program is very easy to use. After starting, it is better to select the default filter, i.e. record all accesses to the registry, and then, in the main program window, select unnecessary process and using the right mouse button call up the context menu - Exclude process - information about accessing the registry this process will not be output. And in the same way, filter out other processes that are not of interest to you.
When working with the program, you can use the File, Edit, Options menu or the keyboard shortcut:
CTRL-S - save results
CTRL-P - properties of the selected process
CTRL-E - enable/disable monitoring
CTRL-F - search by context
CTRL-C - copy selected line to clipboard
CTRL-T - change time format
CTRL-X - clear the monitoring results window
CTRL-J - launch the registry editor and open the branch specified in the Path column. The same action is performed when double click left mouse button. A very useful feature that saves a lot of time.
CTRL-A - enable/disable automatic scrolling
CTRL-H - allows you to set the number of lines of monitoring results
Another very useful feature is to get a log of accesses to the registry during the boot process of the operating system.
To do this, select the menu Options-Log Boot. The program will display a message that Regmon is configured to write registry accesses to a log file during the next OS reboot:

After rebooting the OS, in root directory system (C:\Windows) there will be a Regmon.log file with a log of monitoring results. Logging mode will continue until the logged on user runs Regmon.exe and only occurs for one system reboot. Of course, the contents of the log will not fully reflect absolutely all accesses to the registry. Since Regmon in Log Boot mode is installed on the system and, after a reboot, starts as a driver, all access to the registry that occurred before it started will not be recorded in the log. However, most of them will still get there, and you will see that there will be several hundred thousand such requests.

To save and restore the registry, use the "Disk and Files" - "SystemSaver" section. To maintain and optimize the registry - "System Registry" - "RegistryFixer" and "RegistryDefrag".
In addition to the Startup folder, the following registry keys are used to launch programs:HKLM\Software\Microsoft\Windows\CurrentVersion\Run
HKLM\Software\Microsoft\Windows\CurrentVersion\RunServices
HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKLM\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
The last 2 sections (...Once) differ in that the programs written in them are launched only 1 time and after execution the key parameters are deleted..
Entries in HKLM apply to all users of the computer. For the current user, startup is determined by the keys in the HKU section:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Example of HKLM\...\RUN section: 
In the right window you see a list parameters, whose values are a string referencing the program. When the user logs in, all listed programs will be executed. Remove the parameter - the program will not start. But not everything can be deleted. Experiment by changing the exe extension to ex_.
In addition to the programs that are launched when a user registers in the system, a huge number of others are launched, which are not always obvious - these are system services (services), various drivers, shell programs (Shell), etc. In addition to useful (and sometimes useless) programs, they can be executed using automatic startup and viruses that have entered the system. More details about viruses. Possible points automatic start There are a huge number of executable modules, and to search for them in the registry it is more convenient to use special programs- startup monitors, the most popular of which is, which has a wider range of capabilities than utility program MSConfig, included with Windows.

No installation required. Just download Autoruns, unzip it and run the Autoruns.exe file (autorunsc.exe - console version). The program will show which applications are configured to start automatically, and will also present a complete list of registry keys and file system directories that can be used to set automatic startup. The items that Autoruns shows belong to several categories: items that automatically start at logon, Explorer add-ons, Internet Explorer add-ons (including Browser Helper Objects (BHOs)), DLLs application initialization, element substitution, objects executed at early boot stages, Winlogon notification DLLs, Windows services and Winsock multi-tier service providers.
To view automatically launched objects of the required category, just select the desired tab.
To search for entries in the registry related to the selected object, just use the "Jump to" item context menu, called by the right mouse button. The Registry Editor will launch and the key that allows it to launch will open.
Drivers and services.
Information about drivers and system services (services) is in the section HKLM\System\CurrentControlSet\Services
Each driver or service has its own section. For example, "atapi" - for a standard driver IDE controller hard drives, "DNScache" - for the "DNS client" service. Purpose of main keys:
DisplayName- display name - what you see as a meaningful name when using, for example, control panel elements.
ErrorControl- error handling mode.
0 - ignore (Ignore) if there is an error loading or driver initialization, no error message is displayed and the system continues to operate.
1 - normal (Normal) error processing mode. System operation continues after the error message is displayed. ErrorControl settings for most device drivers and system services are set to 1.
2 - special (Severe) mode. Used to ensure that the last known good configuration is loaded (LastKnownGood).
3 - critical error. The download process stops and a failure message is displayed.
Group- the name of the group to which the driver belongs, for example - “Video adapters”
ImagePath path and name of the executable driver. Driver files usually have a .sys extension and are located in the \Windows\System32\DRIVERS\ folder. Service files are usually .exe and are located in \Windows\System32\.
Start boot and initialization control. Determines at what point in the system boot the driver or service is loaded and initialized. Start values:
0 - BOOT - the driver is loaded by the bootloader.
1 - SYSTEM - the driver is loaded during kernel initialization.
2 - AUTO - the service starts automatically when the system boots.
3 - MANUAL - the service is started manually.
4 - DISABLE - disabled.
Drivers are loaded and services are started with Start parameters from 0 to 2 before the user registers in the system. To disable a driver or service, just set the Start value to 4. Disabling drivers and services by editing this registry key is a rather dangerous operation. If you accidentally or unknowingly disable a driver or service, without which loading or operation is impossible, you will get a system crash (most often, a BSOD blue screen of death).
Drivers and services for safe mode.
When the operating system boots, a set of control parameters from the current configuration section is used to initialize drivers and services HKLM\System\CurrentControlSet
If problems arise with the operation of the operating system, safe boot mode is often used ( Safe Mode). Difference this mode from a normal boot, is that the minimum required configuration of drivers and system services is used, the list of which is specified in the section:
HKLM\System\CurrentControlSet\Control\SafeBoot
Subsections:
Minimal- list of drivers and services that start in Safe Mode
Network- the same, but with network support.
In addition to the HKLM\System\CurrentControlSet section, the registry also contains
HKLM\System\CurrentControlSet001
HKLM\System\CurrentControlSet002
In their structure, they are identical to HKLM\System\CurrentControlSet, and are intended for the additional possibility of restoring system functionality by loading the Last Known Good Configuration of the system. Possible options for loading control sets are determined by the contents of the section:
HKLM\System\Select

Current- the control set that was used for the current load.
Default- control set that will be used at the next boot.
LastKnownGood- control set that will be used if the Last Known Good Configuration boot mode is selected.
Failed- a failed control set that will be created if the Last Known Good Configuration boot mode is selected.
After successful download and user login, data from CurrentControlSet and ControlSet001 is copied to ControlSet002. When the configuration changes, data is written to CurrentControlSet and ControlSet001. If changing the settings caused the system to crash, it is possible to restore it by using the last successful boot option, which takes data from ControlSet002. After successfully booting into this mode, a new subkey will appear with a control set, ControlSet003, in case you need to use Last Known Good Configuration again. Each time you use Last Known Known Configuration, the value of ControlSet00x will be incremented.
We limit user access to resources.
In most cases, in order for changes made to the registry to take effect, you need to reboot or log out and log back in. The parameters in the HKEY_CURRENT_USER section apply to the current user of the system. Settings in the HKLM section apply to all users. Hiding logical drives
Open the section:HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer
and add the parameter to it NoDrives DWORD type. The parameter value determines the A-Z drives to be hidden. The presence of a "1" starting with the least significant bit of the double word means there is no logical drive in "My Computer"
00000001 - no drive A, 00000002 - no drive B, 00000004 - no drive C, 0000000F - no drives A-F
I will add that disks hidden in this way are not visible only to Explorer and may be accessible in other programs (in FAR, for example). But other programs can be hidden or banned - more on that later.
Changing the menu of the "START" button
NoRun=dword:00000001 there is no "Run" buttonNoLogOff=hex:01 00 00 00(not dword but hex) no "End session"
NoFind=dword:00000001 - there is no “Find” item
NoFavoritesMenu=dword:00000001 no "Favorites"
NoRecentDocsMenu=dword:00000001 no "Documents"
NoSetFolders=dword:00000001 there is no "Control Panel" in the "Settings" submenu
NoSetTaskbar=dword:00000001 no "Taskbar" there
NoPrinters=dword:00000001 no "Printers" in Control Panel
NoAddPrinter=dword:00000001 no "Add printer"
NoDeletePrinter=dword:00000001 no "Delete printer"
NoDesktop=dword:00000001 Empty desktop
NoNetHood=dword:00000001 no "Network Neighborhood"
NoInternetIcon=dword:00000001 there is no Internet icon on the Windows desktop
NoTrayContextMenu=hex:01,00,00,00 -Disable right-click menu on taskbar
NoViewContextMenu=hex:01,00,00,00 - Disable the right-click menu on the Desktop: To turn it back on, replace 01 with 00.
NoFileMenu=hex:01,00,00,00 hide "File" in the top menu bar of Explorer
ClearRecentDocsOnExit=hex:01,00,00,00 do not save the list of recently opened documents upon exiting the system.
The following settings apply to the registry key
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\ Network
NoNetSetup=dword:00000001 disables access to the Network icon in Control Panel
NoFileSharingControl=dword:00000001 hides the file and printer sharing management dialog box, preventing users from managing the creation of new file or printer sharing
NoNetSetupIDPage=dword:00000001 hides the "Identity" tab
NoNetSetupSecurityPage=dword:00000001 hides the "Access Control" tab
NoEntireNetwork=dword:00000001 hides the "Entire Network" element in Network Neighborhood
NoWorkgroupContents=dword:00000001 hides all content of the Workgroup in the Network Neighborhood
The following settings apply to restrictions for all users because the HKLM key is used rather than the HKEY_CURRENT_USER key. To edit data you must have system administrator rights
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System
NoSecCPL=dword:00000001 disables access to the Passwords icon in Control Panel
NoAdminPage=dword:00000001 hides the "Remote Control" tab
NoProfilePage=dword:00000001 hides the "User Profiles" tab
NoPwdPage"=dword:00000001 hides the "Change Passwords" tab
NoDispCPL=dword:00000001 disables access to the Display icon in Control Panel
NoDispAppearancePage=dword:00000001 hides "Appearance" in the screen properties window
NoDispBackgroundPage=dword:00000001 hides "Background" in the screen properties window
NoDispScrSavPage hides the "Screen Saver" in the Display Properties window
NoDispSettingsPage=dword:00000001 hides "Settings" in the screen properties window
NoConfigPage=dword:00000001 hides "Hardware Profiles" in the System Properties window
NoDevMgrPage=dword:00000001 hides the "Devices" tab in the system properties window
NoFileSysPage=dword:00000001 hides the " button File system..." on the "Performance" tab in the system properties window
NoVirtMemPage=dword:00000001 hides the "Virtual memory..." button on the "Performance" tab in the system properties window
=dword:00000001 ban Regedit.exe or Regedt32.exe
Some of the listed prohibitions on user actions are used not only system administrators, but also viruses that have entered the system. Typically, data is written to the registry that blocks the ability to search and remove embedded malicious software and, as a final touch, prohibits the launch of the registry editor (DisableRegistryTools). As a result, even with administrator rights, the user is not able to do anything with his own registry. An attempt to launch the editor ends with a message like this:

Of course, a user, especially an administrator, should be offended when “Editing the registry is prohibited by the system administrator.” So I added another small section:
We bypass user access restrictions to resources.
All of the above restrictions may apply to either a specific user or all users of the system, or rather their accounts. However, every Windows OS has one more Account, whose rights, to some extent, are even higher than the rights local administrator- local system account (Local System Account) on behalf of which system services are launched even before the user logs into the system. If the program (the same regedit.exe) is run with Local System rights, then no restrictions associated with the accounts of any real users will apply. I already described how to launch the registry editor with the rights of a local system account using the PSExec utility at the beginning of the article, and there I also posted a link to the download page and description of the PSTools package. For those who do not need to download the entire package and need, without understanding the intricacies, to simply bypass the restrictions - step-by-step instructions:psexec -s -i regedit.exe
To operate psexec.exe you need to have administrator rights, i.e. the user must be a member of the Administrators group
Of course, you can come up with other options for bypassing the restrictions, such as downloading using Winternals ERD Commander and editing the problematic registry, or using the command line utility REG.EXE (Download a bat file to unlock the registry editor and task manager), or an editor registry from a third-party manufacturer, but this method is the most unusual, simple and fast. The uniqueness of the solution to the problem, as a rule, gives the advantage that there are no restrictions against your actions to circumvent, or there are not yet pre-prepared countermeasures.
By the way, this method can be used not only to launch regedit.exe, but also other programs - Explorer (Explorer.exe) for example
psexec -s -i C:\WINDOWS\EXPLORER.EXE
which will allow you to access directories and files that are inaccessible to a real user, such as hidden system folder System Volume Information.
A very good way to bypass the restrictions is to use a third-party registry editor.
Resplendent Registrar Registry Manager - approximately 3MB - in the "Lite Edition" - free registry editor with a user-friendly interface and useful additional features for searching, monitoring, defragmenting, saving and restoring the registry.
A long-deleted program appears in the list of installed programs.
This usually happens if you removed the program manually rather than uninstalling it, or the uninstaller glitched. You can correct the situation by editing the section:HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall
I constantly have to specify the path to the Windows distribution
Find a sectionHKLM\Software\Microsoft\Windows\CurrentVersion\Setup
and in the parameter SourcePath specify the path to your distribution - the string value "D:\install" . If you often change system settings and have a lot of disk space, drop the distribution into some directory and register it in SourcePath.
Problems with Russian font on some programs
This is especially true on non-Russian operating systems, such as Windows NT 4.0 Server. Even if you installed Russified fonts and specified Russia in the regional settings, problems with Cyrillic fonts may arise. Open sectionHKLM\Software\Microsoft\Windows\CurrentVersion\FontSubstitutes
and enter the parameters:
parameter System,0 value System,204
parameter Courier,0 Courier value,204
parameter Arial,0 Arial value,204
parameter Courier New,0 Courier New value,204
parameter Times New Roman,0 Times New Roman value,204
Most likely, these parameters are already there, but instead of 204 it is 238. For Windows 9X there is no such registry section and you need to edit the WINDOWS\win.ini file section.
It may also help to add a parameter to the HKLM\System\CurrentControlSet\Control\Nls\CodePage section "1252" ="CP_1251.nls"
Removing the password from the screen saver (ScreenSaver)
The default desktop settings for a profile are set by the registry key settingsHKEY_USERS\.DEFAULT\Control Panel\Desktop
Current user desktop settings - registry key
HKCU\Control Panel\Desktop
To remove the password from the current user's desktop screensaver, you need to open the registry key
HKCU\Control Panel\Desktop
and set the key value ScreenSaverIsSecure equal to zero.
To disable the screensaver - set the value to 0 ScreenSaveActive
Creating your own window when logging in
This is useful when you need to warn the user about something. Section HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WinlogonOptions:
LegalNoticeCaption= for example "Attention!" window title text
LegalNoticeText ="From the 25th to the 30th of each month you need to change your password" text in the window
Clearing the previous username
Section HKLM\SOFTWARE\Microsoft\Windows NT\ CurrentVersion\WinlogonDontDisplayLastUserName=dword:00000001
Prohibition of launching the Registry Editor and Task Manager.
To prevent any user from starting the registry editor, use the section HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system=dword:00000001 is not allowed to run
=dword:00000000 allowed to run
DisableTaskMgr- =dword:00000001 is prohibited from running
DisableTaskMgr- =dword:00000000 allowed to run
To limit the launch of the Registry Editor and Task Manager for the current user, similar values are set in the section
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies
Required password entry in Windows 9X
Must be installed Microsoft client Network. You can no longer log in by pressing ESCSection HKLM\Network\Logon
Parameter MustBeValidated=dword:00000001
Change how your computer behaves when shutting down
Section HKLM\System\CurrentControlSet\Control\ShutdownParameter FastReboot equal to 0 - normal shutdown, equal to 1 - accelerated, often leading to a reboot
Changing the default language in the login window
If the Russian keyboard layout is used in the password entry window, you can change this by editing the HKEY_USERS\.DEFAULT\Keyboard Layout\Preload section. It has 2 string parameters - "1" and "2".If the values are equal:
1=00000409
2=00000419
then the layout in the login window will become English.
If you assign the values to the parameters the other way around ("1"=00000419, "2"=00000409) - then the layout will become Russian.